Machine Token
The Machine Token feature allows or restricts Windows, MacOS, Android, and iOS endpoints from accessing private and internet applications without requiring user authentication to the Atmos endpoint agent.
The following states are supported:
1. Machine Authentication
- In this state, no user is currently logged into the machine. This typically applies to shared devices or newly deployed devices. If a token is present in a designated location, the agent will use that token to authenticate upon startup to HPE Aruba Networking SSE(without a user login to the Atmos agent). The policy, governed by the Axis IDP Machine Token can enforce ZTNA and SWG both before and after login.
2. Authenticated User and Expired Authenticated User - Post Agent Login
- Managed Device - When the machine token is set, users will receive user-based policies as long as they are authenticated. After authentication expires, the agent will enforce token policies, determined by the Axis IDP Machine Token, which can include ZTNA and SWG enforcement.
- UnManaged Device - When the machine token is not set, users will receive user-based policies as long as they are authenticated. After authentication expires, the machine will only receive SWG "ANY" identity rules for generic SWG protection (By Default). This behavior is configurable.
Note
- When a user logs out of the Atmos agent, all policy enforcement stops.
- There is a grace period of 7 minutes between policy transitions after authentication expiration.
- Tokens can be shared across multiple devices.
- Minimum agent version 3.50+
Configuration Steps:
- Creating an Axis IDP Machine Token to be used to identify the connected Atmos agent(s).
- Setting a policy for the Axis IDP Machine Token Identity.
- Using an MDM solution / Manually set a registry key and install the Axis agent on the device.
1. Creating the Axis IDP Machine Token
The Machine Token requires a special user account for secure, conditional access to resources.
- First, create the Machine Token account in the Axis IdP by navigating to Settings -> Axis IdP -> Machine Tokens
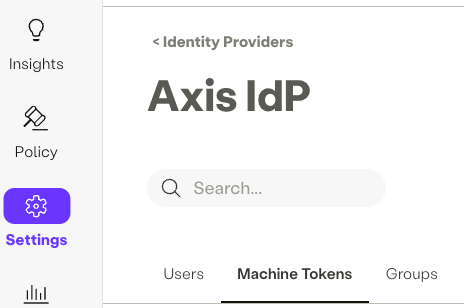
- Select New Machine Tokens
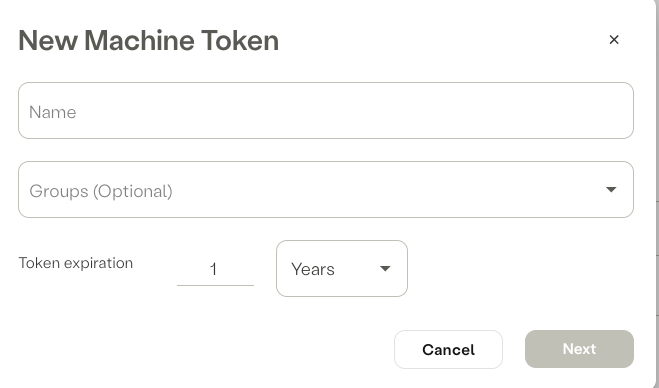
- Name - Enter the name of the token
- Groups - Associate the new token with Axis Identity Groups (optional)
- Token Expiration - Set the token expiration date
- Select Next
- Record the token
- Copy the entire token to a secure place for device configuration
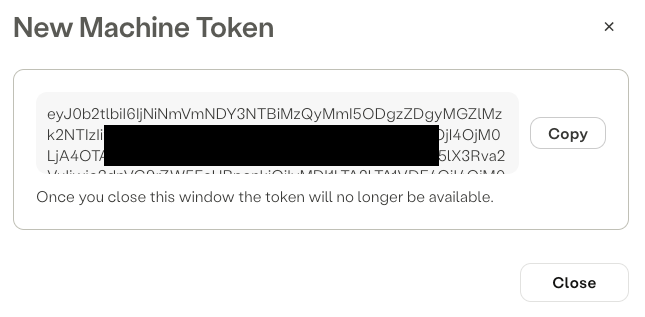
Note
- The token GUID is only available during the creation process
2. Setting a policy rule for the Machine Token
Access to the pre-configuration resources requires creating a new policy rule that allows the Machine Token identity to access the required resources.
- Confirm the internet or private applications required have been created under Settings -> Destinations. If necessary, create the applications (for example, Active Directory Application)
- Create a new policy rule under Policy -> Rules. The rule should allow the Machine Token identity to access the resources from the above steps.
3. Configuring the MDM Solution
The MDM solution is used to pre-stage the Axis agent and Machine Token so that the Atmos tunnel can be started automatically.
- Use the MDM to push and install the Axis agent to the machine. Machine Token requires agent version 3.47 or later. Contact Axis Support ([email protected]) if necessary to enable this version.
-
Windows - Agent version
- Use the MDM to set the registry key to the value of the Machine token obtained from the steps above:
- The key has to be set in the following path: Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Classes\axis
- When creating the new Registry Key, select the "String Value" type.
- Note: If a “PreLogonTunnel” registry key is already present in the above path, delete it.
- New Registry Key Info:
Key: “InitToken”
Value: Generated from the steps above
- Use the MDM to set the registry key to the value of the Machine token obtained from the steps above:
-
Mac - Agent version
- Download the template
- Replace (REPLACE!_STUB_BASE64DEVICETOKEN) with the actual machine token
- Replace UUID1 with new generated uuid
- Replace _UUID2_with new generated uuid
- Save the modified profile to your computer
- Double-click on the file to install locally or push via the MDM install
Note
- For the UUID 1 & 2, the following generator can be used UUID Generator
-
Linux - Agent version
- Place the Machine token in a .txt file in the following path
- /var/lib/AxisSecurity/.init_token
- Place the Machine token in a .txt file in the following path
-
Android Agent version
- using an MDM, pass a configuration key named InitToken with the token as the value, as described in the following doc MDM Ownership Variable
Additional Notes:
- The Windows endpoint must be domain-joined.
- After a successful access to the axis agent, the Pre-Logon tunnel will not re-initiate by default. In order to keep the Pre-Logon functionality after a user has logged in the agent please contact Axis Support.
Updated about 1 year ago
