Firewall Rules for Connector Connectivity
The Atmos Connector requires two connectivity components as shown in the following network topology.
- Connector to Atmos Cloud Connectivity
- Connector to Customer App Connectivity
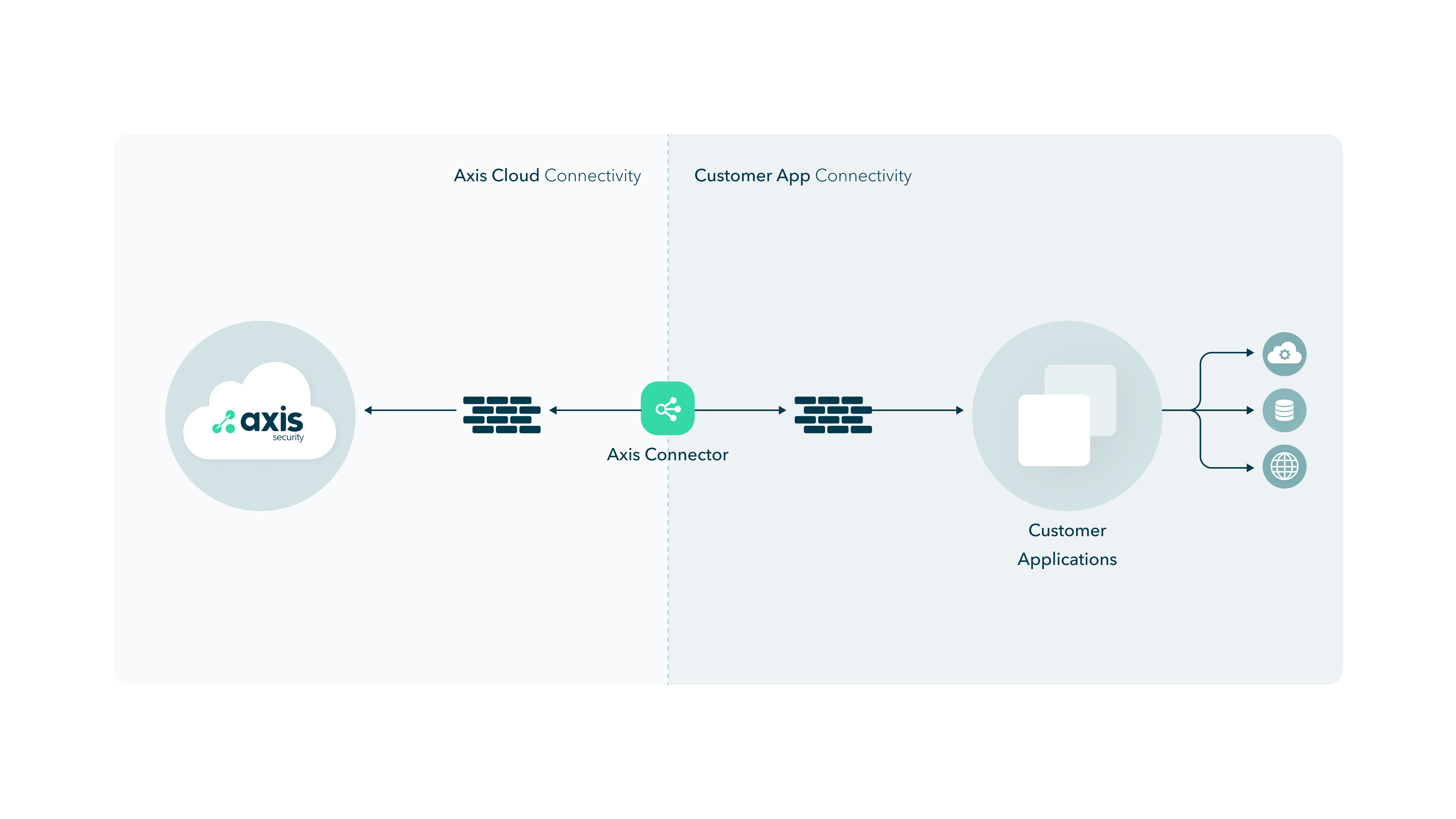
Atmos Connector to the Cloud
To enable service between the Atmos Connector and the Atmos Cloud, configure your firewall and environment to allow the Atmos Connector as shown in the following sections.
Important: If the network you are placing the Connector is on 10.244.0.0/16, contact Axis Support for assistance to change the Atmos Connector 's Kubernetes network configuration to a non-conflicting 10.200.0.0/16 range.
- Connector->DNS (External/Local) - DNS UDP Port 53
- For public IP resolution, including axissecurity.com names.
- Use only secure and trustable DNS servers.
- The DNS server must be able to resolve axissecurity.com addresses.
- Connector->backend-tcp.axissecurity.com - TCP Port 443
- For agentless access to Axis Application Access Cloud.
- IP addresses:
- 3.33.176.114
- 15.197.168.157
- Connector to backend requirements
| Source | Destination | Port |
|---|---|---|
| Connector | backend-udp-geo.axissecurity.com | UDP/443 |
| Connector | backend-udp-ga.axissecurity.com | UDP/443 |
For Agent-based access to the Axis Application Access Cloud using Geo Proximity resolution.
- IP addresses
- 99.83.147.106
- 75.2.111.171
- 20.162.103.106
- 20.165.33.241
- 40.78.142.235
- 4.205.3.154
- 51.16.148.64
- 51.16.206.144
- 34.176.202.93
- 34.91.173.159
- 104.155.208.6
- 34.118.1.144
- 34.166.165.26
- 172.204.25.151
- Mesh Requirements - Open TCP/UDP 443 either by FQDN or by IP addresses listed below.
| Source | Destination | Port |
|---|---|---|
| Connector | wglb-fudp.axisapps.io | UDP/443 |
| Connector | wglb-tls.axisapps.io | TCP/443 |
Connector Mesh IP Addresses (udp and tcp 443):
udp:
104.43.174.49
13.49.62.121
51.20.23.100
34.176.177.8
44.227.58.106
52.32.29.0
35.236.155.73
54.65.137.118
18.178.82.200
51.17.39.107
51.17.33.208
15.229.178.44
54.207.84.244
20.162.101.223
18.100.244.85
18.101.129.233
13.126.49.178
43.204.254.112
46.137.247.99
18.138.174.138
13.244.168.37
13.245.46.43
3.99.85.222
15.156.176.57
13.238.99.141
52.64.24.170
20.165.34.81
34.34.84.152
35.181.75.176
15.236.76.40
18.102.129.134
18.102.136.83
18.135.248.206
13.42.224.82
3.70.84.94
18.158.192.217
3.216.45.167
34.200.35.168
43.218.250.97
43.218.230.132
16.26.9.203
16.50.79.103
51.17.37.204
51.16.81.47
3.28.247.8
51.112.57.75
54.167.16.160
18.215.40.221
3.227.206.139
3.211.60.122
20.151.135.204
34.118.62.113
13.209.157.187
43.200.101.251
18.60.139.213
18.61.46.237
18.167.87.134
18.166.172.153
54.222.169.33
54.223.36.98
54.151.109.232
54.215.87.66
34.166.175.215
172.204.25.75
51.96.182.88
51.96.84.90
78.13.217.251
78.13.238.33
tcp:
100.20.99.222
35.162.100.28
18.169.228.249
35.176.67.178
18.166.94.147
16.163.227.90
34.176.70.186
15.222.42.219
99.79.163.45
15.160.44.80
18.102.139.253
20.162.72.127
51.92.45.62
18.100.188.137
34.91.98.28
51.17.117.115
51.84.19.255
34.80.41.49
13.236.72.129
13.54.232.105
34.118.82.193
16.50.89.25
16.50.31.162
13.84.13.144
13.86.93.72
52.6.143.177
52.73.105.52
34.199.71.206
100.29.78.194
174.129.236.163
3.208.190.227
18.139.213.253
3.0.32.180
13.202.9.173
3.109.57.247
54.232.25.205
52.67.94.160
4.206.169.211
18.184.10.41
52.57.242.46
13.246.134.91
13.247.130.250
140.179.87.124
71.136.72.250
54.176.107.151
52.8.253.101
52.199.67.156
3.114.23.169
16.78.63.78
16.78.66.178
3.29.220.195
40.172.27.95
15.188.166.81
13.39.30.194
15.165.173.20
54.180.62.57
18.61.213.93
98.130.35.12
13.48.16.241
51.20.217.46
34.166.135.25
172.204.25.194
78.13.240.221
78.13.217.202
51.34.1.87
51.96.184.98
Important
In content-filtering firewalls, make sure that WireGuard Protocol is allowed for all entries pointing to backend-udp.axissecurity.com and any other backend-related addresses
- Connector->install-server.axissecurity.com - TCP Port 443
- For installation resources for connector installation and updates.
- IP addresses
- 3.33.174.95
- 15.197.177.140
- Connector->ops.axissecurity.com - TCP Port 443
- For install script and Axis specific resources for connector installation and updates
- IP addresses
- 3.33.143.65
- 15.197.150.161
- In your firewall, whitelist download.axissecurity.com if you are installing the OVA version of the Connector so that you can download it.
- Allow outbound access to NTP servers for time synchronization
- pool.ntp.org
- 2.rocky.pool.ntp.org
- URLs for backend discovery: backend-discovery.axissecurity.com
Important
The Atmos Agent requires additional firewall rules. To learn more, see Atmos Agent Device Prerequisites.
Atmos Connector to Customer Apps
Atmos Connector to Customer Apps
To enable service between the Atmos Connector and your (Customer) applications, configure your firewall and environment to allow the relevant application traffic for each connection between the connector and application servers at the Settings > Applications screen.
Important
Axis Security recommendation is to allow application traffic through the firewall by port number, when possible, to avoid incorrect classification of the traffic by the firewall; for example, if you are using RDP, use port 3389.
Once the firewall and environment is configured, log into the connector and become a root user.
Run the following command to verify that you have a root user privileges.
sudo whoami
Verifying connectivity between the Connector and each service
Here are some examples on how you can verify connectivity between the connector and each service.
Example 1: Testing Connectivity to HTTP and HTTPS Applications
To test connectivity to HTTP and HTTPS applications:
Type the following command in your terminal (shell):
curl test.axisapps.io
curl test.axisportal.io
Note
The output should be a HTML page.
Example 2: Testing connectivity to SSH Servers
To test connectivity to the SSH servers:
Type into the terminal.
ssh -p <port - default is 22> <address>
Note
The output should not be a timeout or a connection refused error.
Example 3: Testing Connectivity to RDP Servers
To test connectivity to RDP servers:
In the terminal, type
telnet <address> <port - default is 3389>
Note
The output should not be a timeout or a connection refused error.
Connector to Apps via Proxy
For deployment scenarios in which a proxy is deployed between the connector and the published application, contact your Axis Security representative for detailed assistance.
- Only Agentless access is supported via proxy to the published app.
- Proxy values will be passed via the installation script (contact Axis)
- Inline services like SSL inspection may need to be bypassed
Atmos Agent to Atmos Cloud
Use the Atmos Agent access approach when a user's device is behind a firewall or on a VPN.
Checking Connectivity to Axis Security
The following script checks connectivity to Axis Security:
curl -kfsSLv -m 5 https://backend-tcp.axissecurity.com
Updated 22 days ago
