Basic Troubleshooting Guide
Use the following procedure to troubleshoot basic Axis Cloud issues.
To learn how to troubleshooting Atmos Agent issues, click here.
| # | Task | Checked? |
|---|---|---|
| 1 | Verify that the Connector is Enabled and the status is Online (available) at the Connector Management screen at Settings > Connector.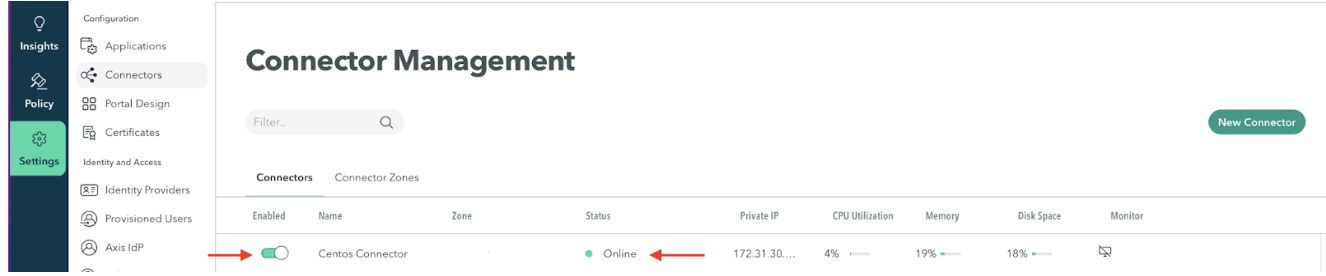 If the connector is not enabled, enable it. If the status is not online after you enable the connector or partially online, go to task 2. See also Troubleshooting Connectors. | |
| 2 | Check your firewalls and proxy rules between the Connector and Axis Cloud IPs. Did your corporate firewall rules or proxy rules change? A common issue is that an organization’s enterprise team reverted some rules on their outbound firewall or proxy where their Connectors are, which causes them to stop communicating with the Axis Cloud. Recommended action: 1. Ask your organization's administrator to validate your firewalls and proxy configuration. 2. Make sure you meet the Connector Deployment Technical Prerequisites. See Firewall Rules for Connector Connectivity. | |
| 3 | Verify the connectivity between the connector and application. 1. Is the application reachable from the connector? To test from the connector, log in to the Connector. A. Issue the commands such as ping, curl, or netcat for your application. B. Confirm that the application’s domain can be resolved in the DNS; for example, run the nslookup or dig commands. 2. Verify that the firewall and security policy allows network traffic between the application and Connector. Review your configuration on your firewall. | |
| 4 | In the Axis management console, go to Settings > Application and check the application configuration.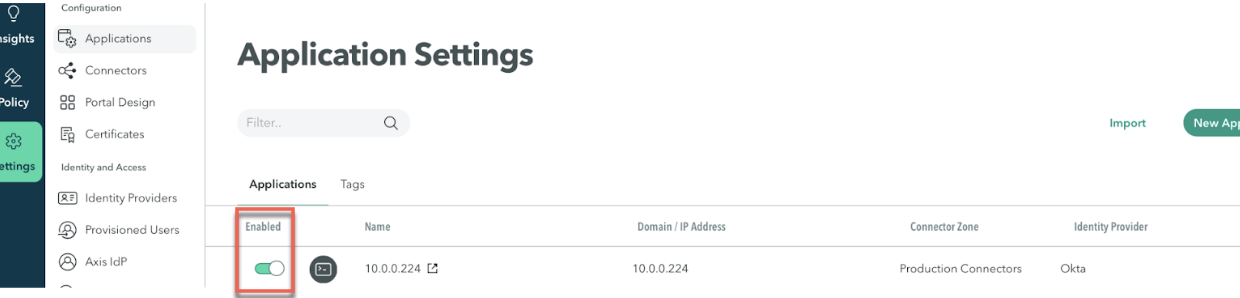 Make sure the application is enabled. Go to the application you are troubleshooting and click the pencil (edit) icon to verify that all the settings are correct. | |
| 5 | Check the policy and verify that the user or user group has access to the application at the Policy > Rules. Verify that the policy settings are correctly configured. Important: When checking the policy, make sure to set it to Allow if you want to allow traffic. Check the following settings: User or User Group: Verify that the user is in the expected user or user group. Make sure the user is correctly defined in the identity. 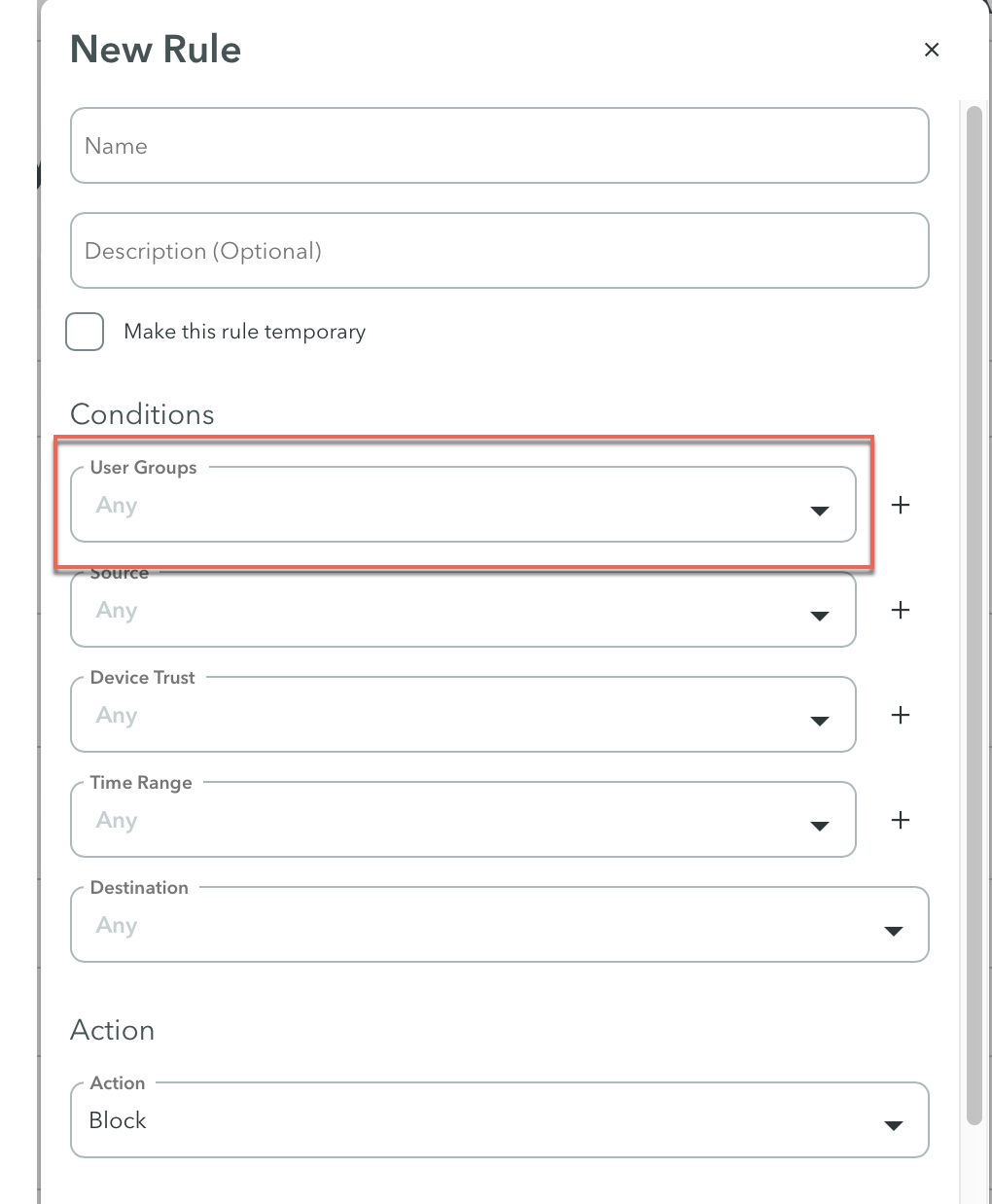 A. Verify your identities or Identity group that are associated with this policy.  B. Go to Policy > Identities and edit the identity to view the users associated with this identity. Destination: Verify that the destination has the correct application or application tag. Source: (This is an optional setting because the default is Any). Is the source misconfigured? Time range (optional setting): Is the time range set correctly? Device Trust: (optional setting) If you have configured device trust: Device Trust for Clientless: If you are using device trust for clientless, check that you are using the correct Client Certificate. Atmos Agent Device Trust: If you are using the Atmos Agent, see Atmos Agent Enrolled Successfully but user can’t access applications. To learn more, see Best Practices for Configuring a Policy and Deployment Considerations and Best Practices. | |
| 6 | Check your identity provider. Verify that the policy is mapped to the correct identity provider at the Settings > Applications. | |
| 7 | In the Insights > Dashboard session section, look for a session that matches the traffic you are trying to send. |
Updated over 3 years ago
