Adding Policy Rules
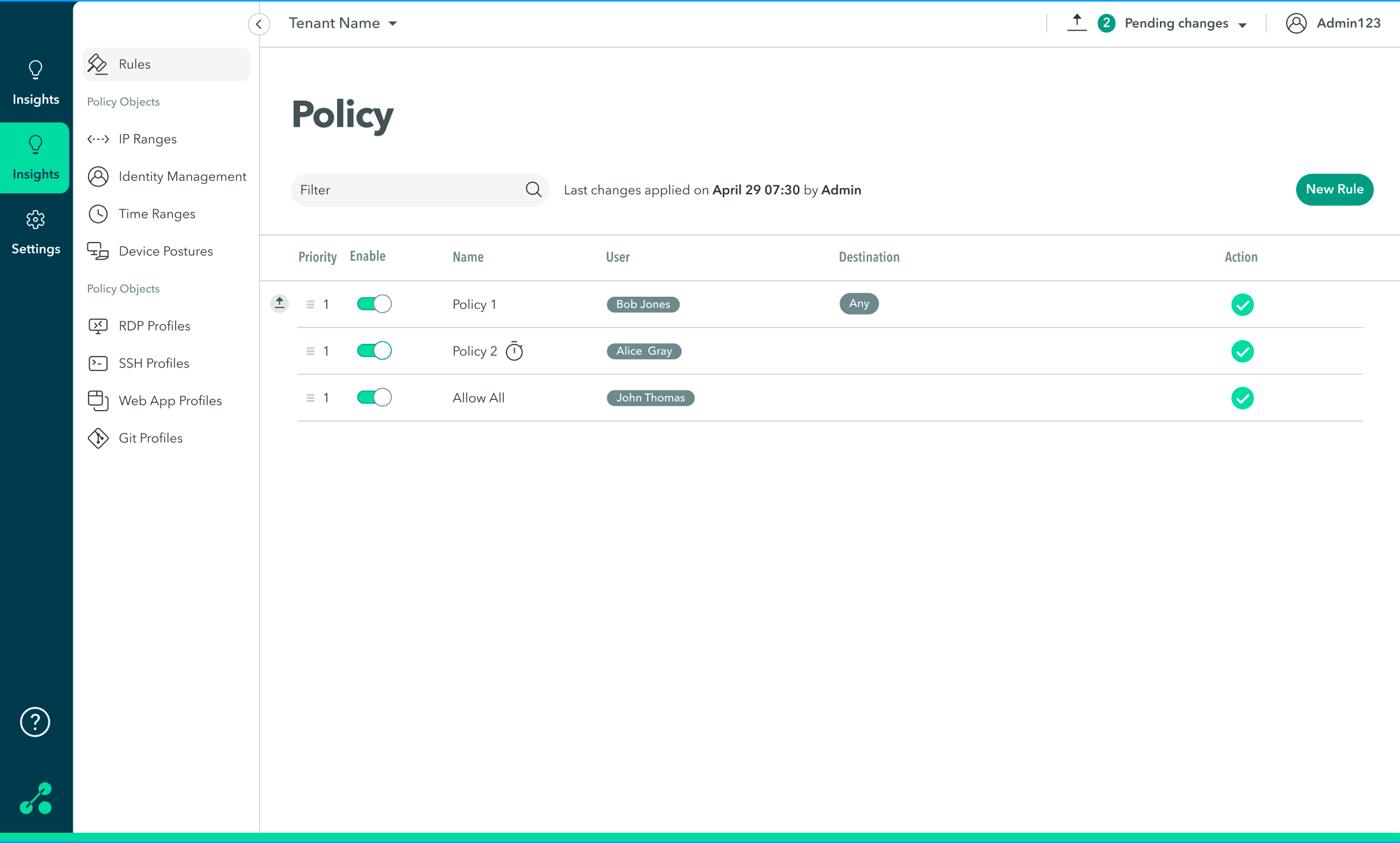
The Policy Screen
Axis evaluates Policy Rules to specific Destinations (Applications or Application Tags) on a first-match principle. For instance, when a user attempts to access a specific application, Axis begins evaluating all of the configured policies starting with the first rule in a set of policy rules. As soon as it finds a policy that matches the criteria that were specified in a rule, it enforces that policy rule and disregards all other rules that follow, including any lower-priority or conflicting rules. If no rule was matched, the default rule is chosen which is always set to "Block".
- Click the toggle to enable or disable a rule.
- Change priorities by clicking the icon and moving the rule to another location in the list.
- Edit a policy or delete it by hovering over the area next to the rule and selecting edit or delete.
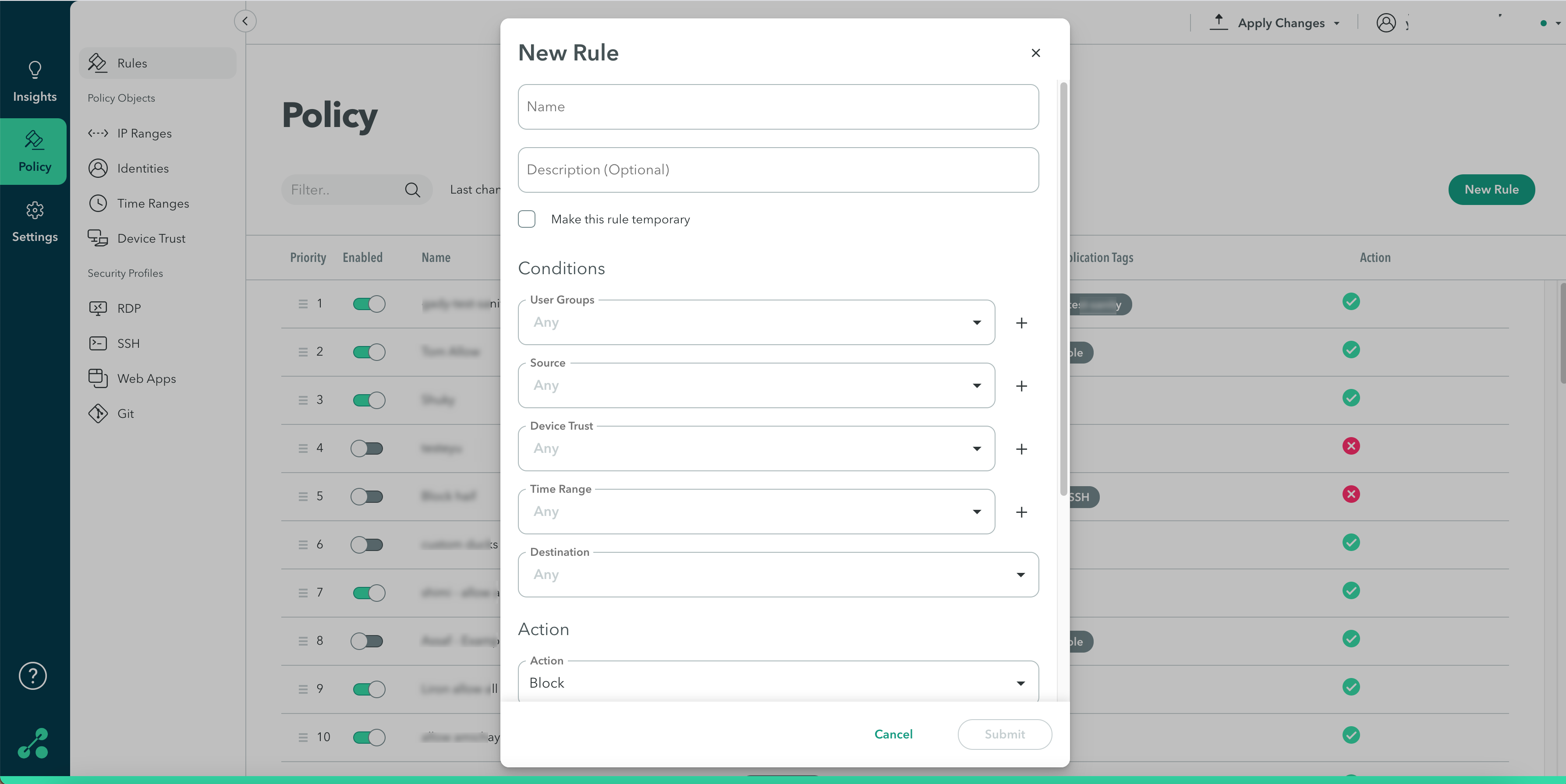
Adding a New Rule
- In the Management Console, go to Policy -> Rules -> Add Rule.
Add name and description. - Click the box next to Make this rule temporary if you wish to create a temporary rule. Select a date and time range.
- Add Conditions.
You can apply the following conditional access criteria to a rule as described in the following table.
Components
The following table describes each condition, its role, and capabilities.
| Condition | Description |
|---|---|
| User Group | Select a User Group from the drop-down menu or click add Add.png to use an Okta identity, an Axis IdP identity, custom SAML Query or identity group. |
| Source | Select a Source from the drop-down menu or click add Add.png to add a new IP range IP that users can access. Select a Geolocation to restrict users restrict from only accessing resources from a location; or example, Germany. |
| Device Trust (Device Posture) | Select a Device Trust from the drop-down menu or click add to add an Atmos Agent Posture or a Client Certificate. For information on Atmos Agent Device Posture, click here To have a condition that is applied to Mac and Windows OS on the same rule: 1. Apply an “OR” condition between the Mac and Windows OS since there will never be an “AND” condition. 2. Create a rule that is Windows-specific and another rule that is Mac-specific. 3. Combine rules by choosing them both. |
| Time Range | Select a Time Range from the drop-down menu or click add Add.png to add a new Time Range Configure a time range that users can access a protected resource. |
| Destination | Specify what users can access: Applications: Select which applications users can access. Web Categories: Select the website type (category) the users can access. To view a list of web categories go to Policy-> Web Categories. Note: This is a limited release feature. For more information contact Axis Security Support: [email protected] App tags: Select a group of applications users can access. |
Note: If all the Conditions are left default/blank they are set to match "Any". You can remove a condition by hovering over the condition and clicking remove icon.

Action
Under Action, select whether the rule blocks or allows access.
Profiles
If no profile is selected, the system will refer to the default profile.
- Select an RDP profile from the drop-down menu or click add to add a new RDP profile.
- Select an SSH profile from the drop-down menu or click add to add a new SSH profile.
- Select a web app profile from the drop-down menu or click add to add a new web app profile.
- Select a Git profile from the drop-down menu or click add to add a new Git profile.
Click Submit.
Click Apply Changes in the top menu bar.
Note
To commit your changes, navigate to the top-right menu, click Apply Changes, then select Commit Changes.
Updated over 3 years ago
