About Policies
A Policy is a collection of rules which provide granular access to your apps depending on a range of parameters. For example, access can be defined based on the destination application groups of the requester.
Atmos enforces policies continuously; when a user's session no longer adheres to a policy rule, it is terminated immediately. Click here to learn more about continuous policy enforcement.
Policies define the following:
- Who can access a application
- Which applications users can access
- When users can access a application
- From where users can access an application, geo location; IP address range
- If users are allowed to access an application, based on the device posture, i.e. it is patched, or does it have a firewall enabled.
- The level of access that a user can have during the connection, i.e. are they allowed to perform certain actions and how often they have to re-authenticate.
- Whether users are explicitly blocked from accessing one or more applications.
- How users can access an application (Axis Agent, alientless)
A rule consists of a set of modular policy objects called Conditions. Admins can either create Conditions in advance, for later use, or in the course of defining Policy Rules. Admins can also create a Security profile to restrict user activity by protocol. For example, a Rule may block a file transfer during an RDP connection based on a more restrictive Profile.
Conditions include:
- IP Ranges
- SAML Queries and SAML Query Groups
- Device Postures. See Device Trust and Configuring the Atmos Agent Device Posture
Security Profiles are part of a policy and include:
Architecture
The following diagram describes the policy definition hierarchy architecture for creating a policy.
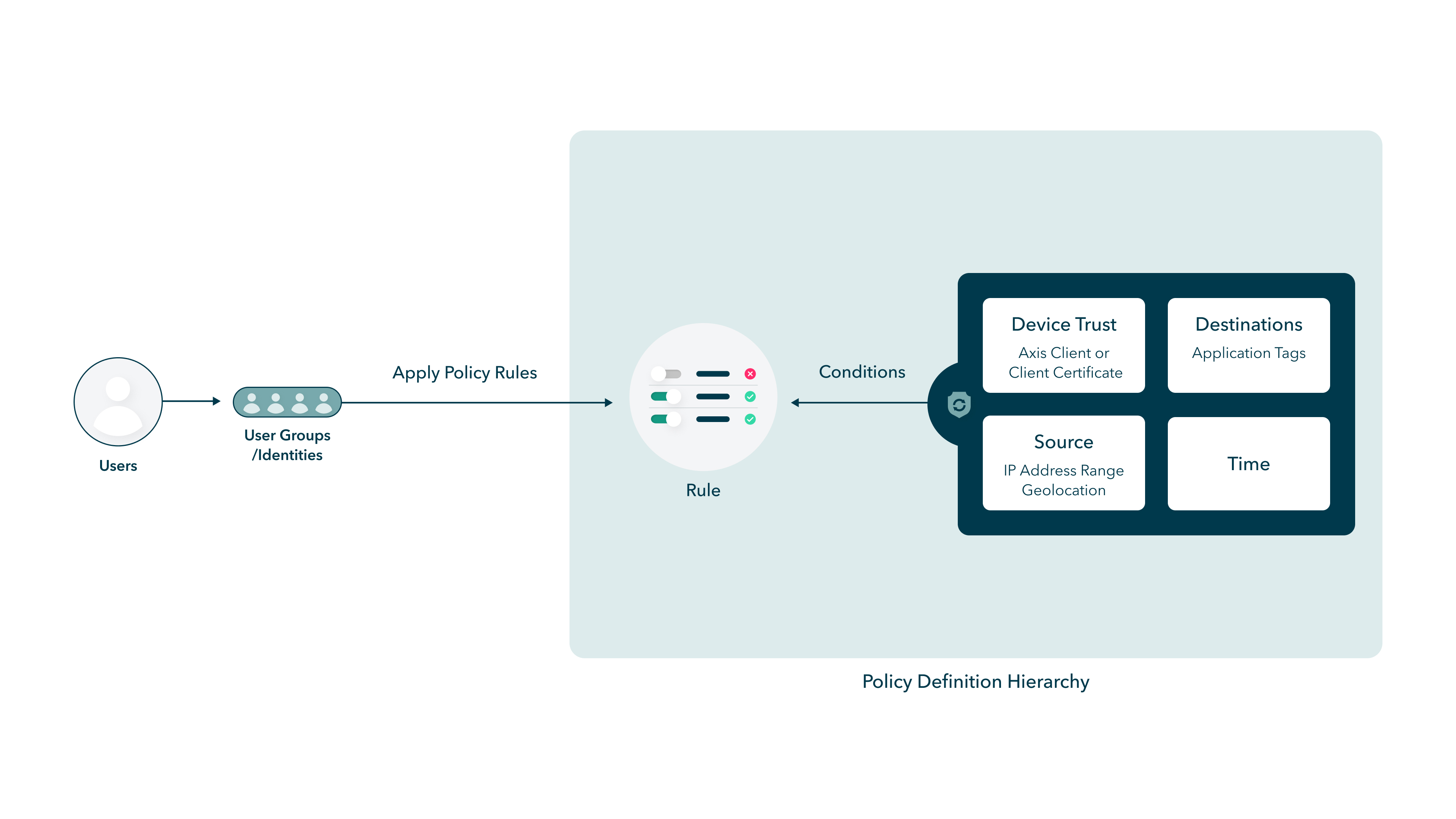
A rule consists of a set of policy objects called Conditions.
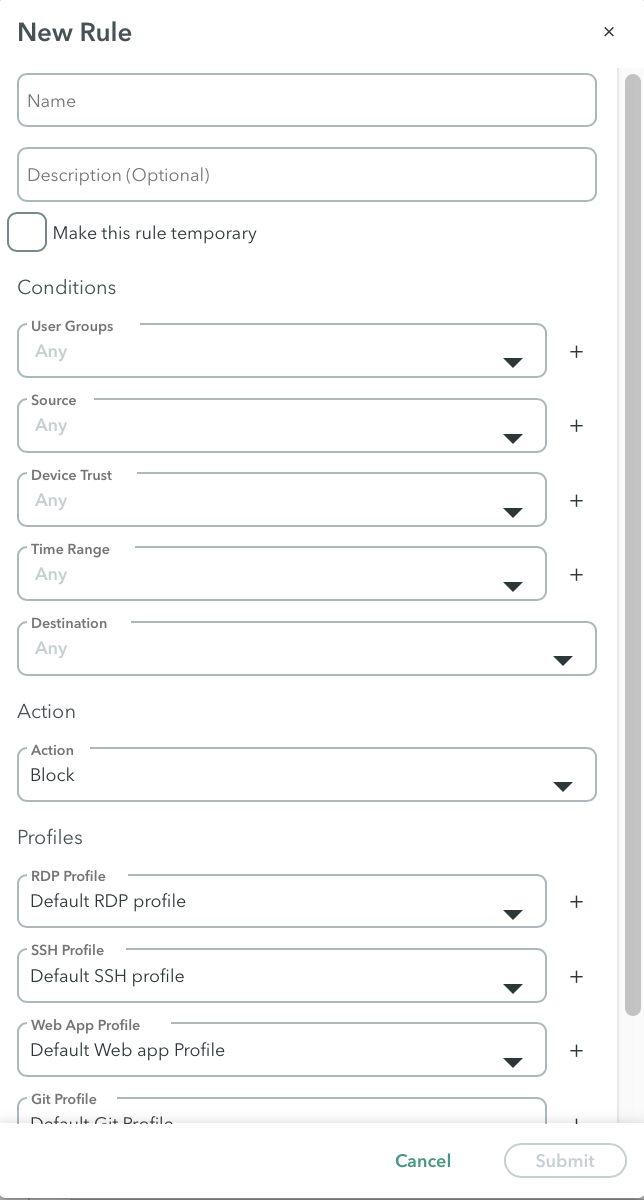
The Policy Table
The Policy table presents information about the different rules in the tenant at-a-glance:
Note
You can filter rules by hovering over a field and clicking the filter icon.
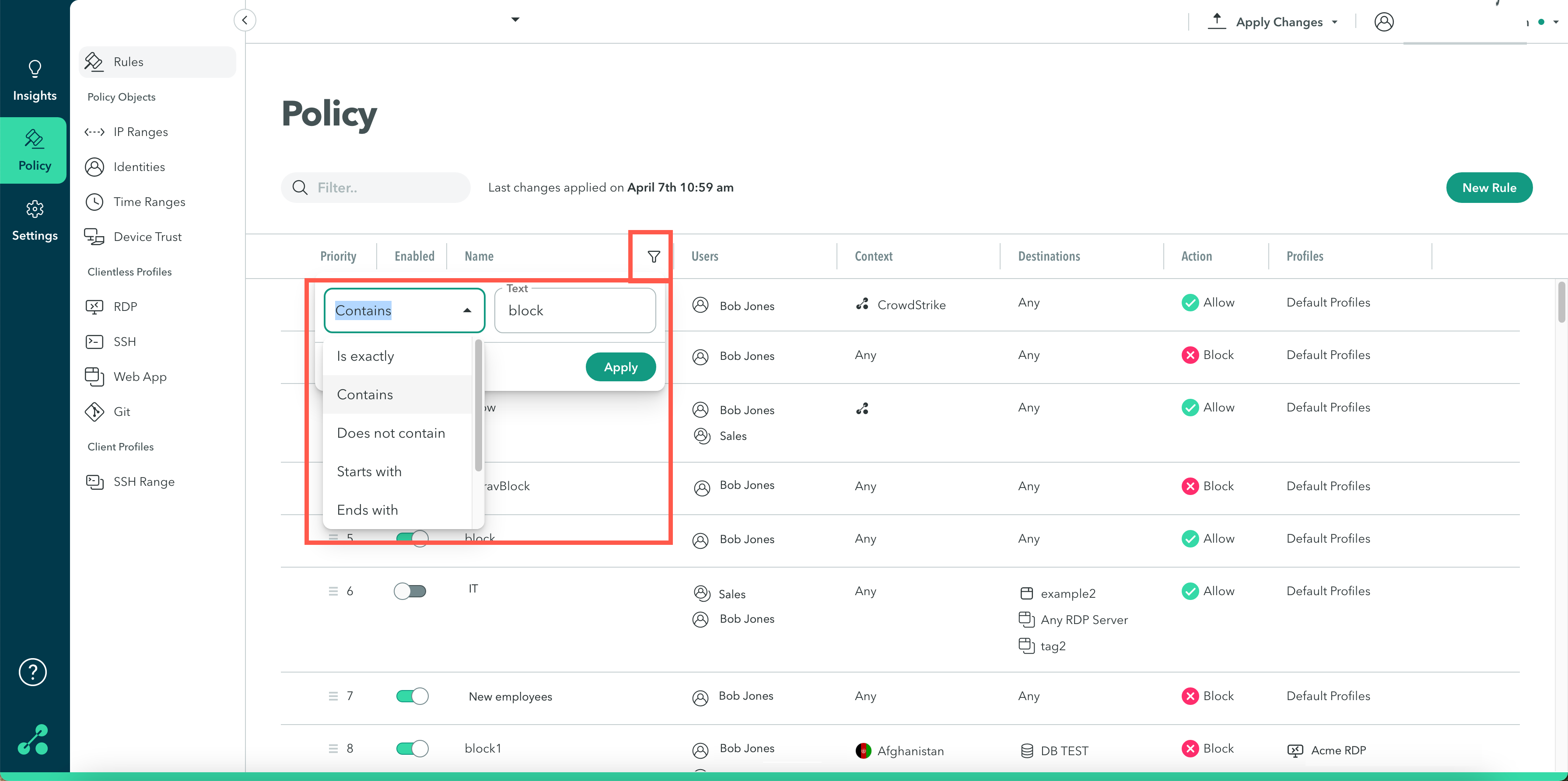
The Context column provides information about the following:
a. Device Trust (Device Posture and Agent certificates)
b. Source (IP Ranges and Geolocation)
c. Time range
The Destinations column provides information about the applications or application tags associated with the rule.
The Profiles column provides information about the security profiles associated with the rule.
Updated over 3 years ago
