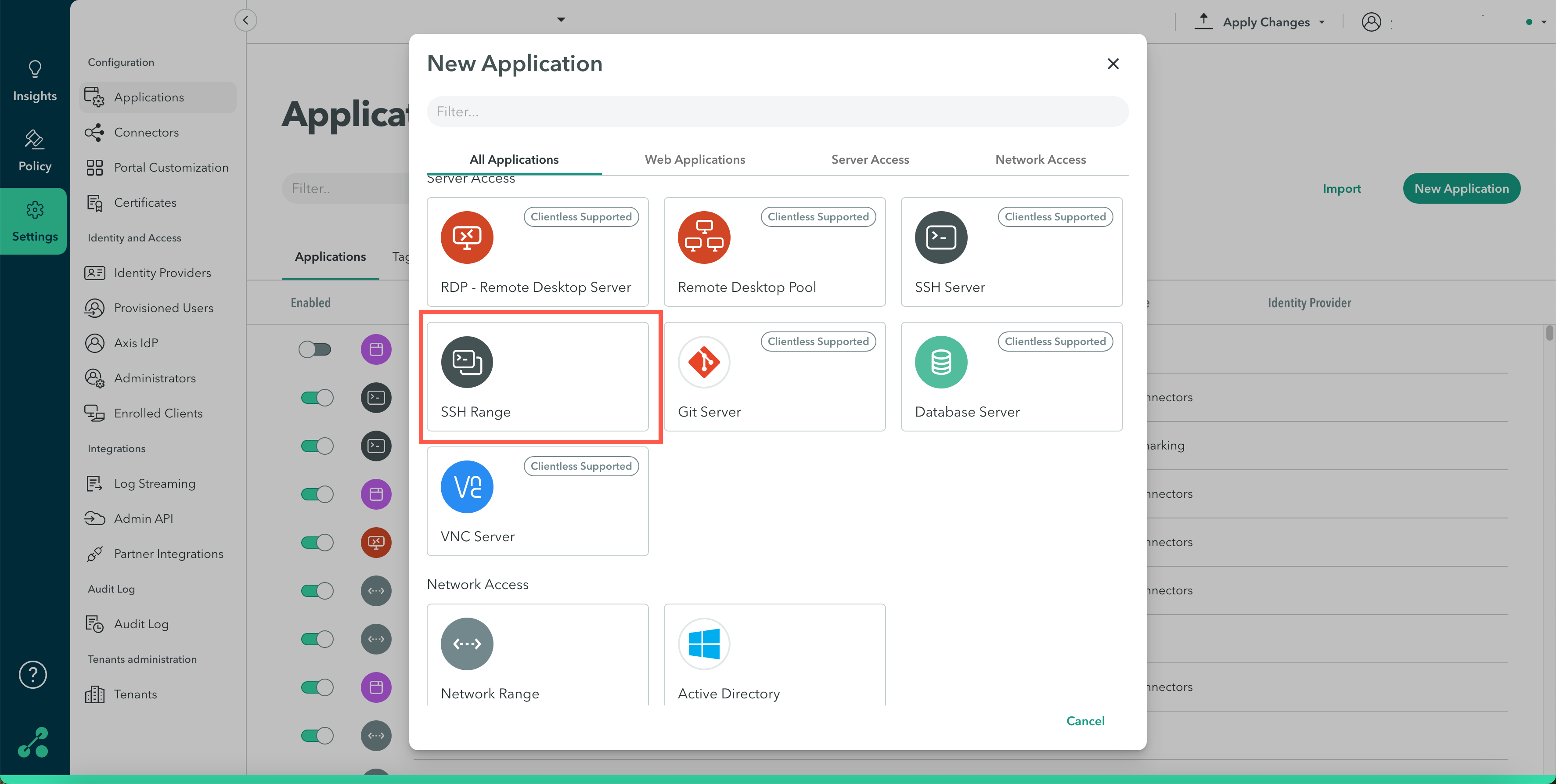
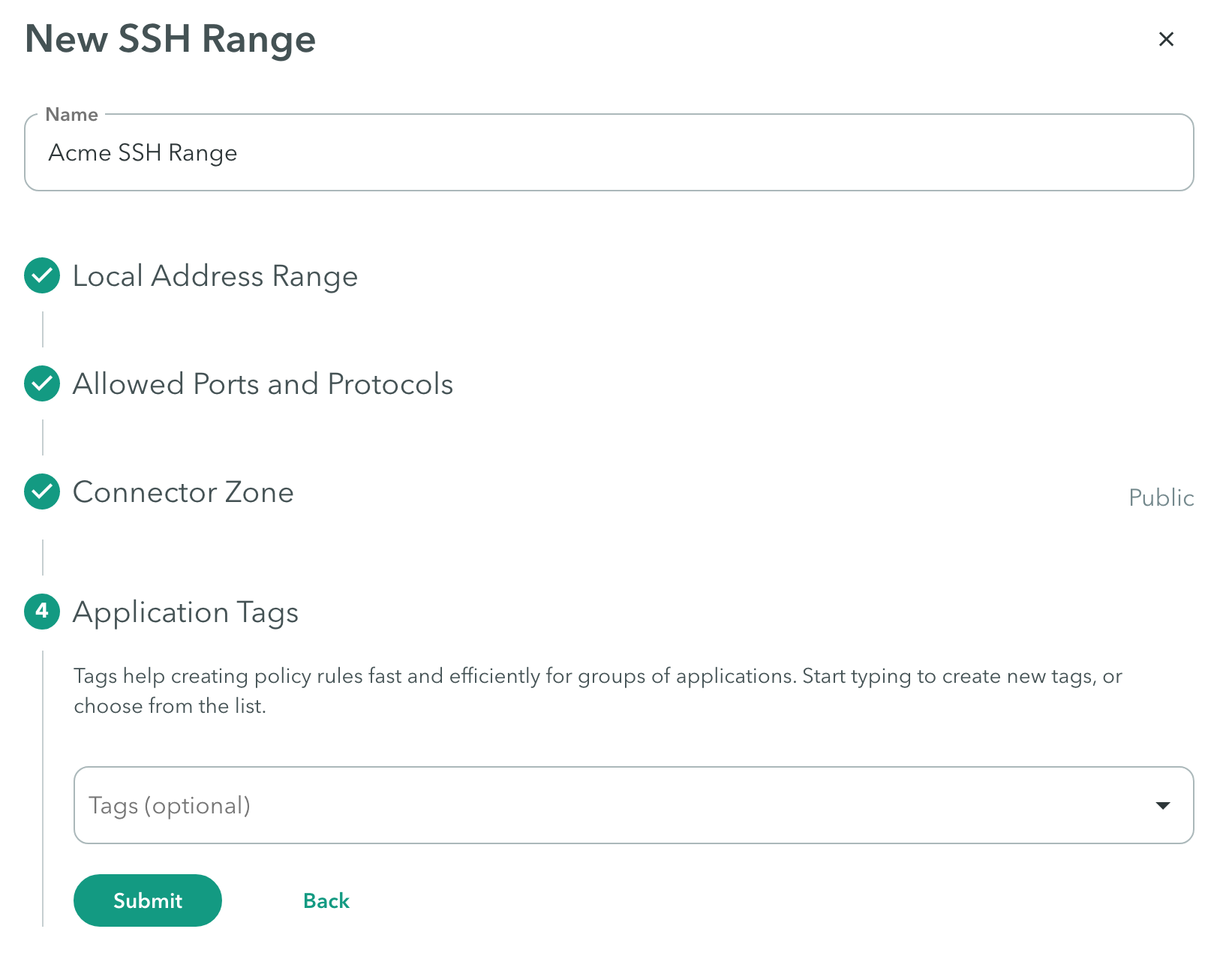
Step 1: Adding an SSH Range Application
This section describes how to add an SSH Range Application.
To add an SSH Range Application:
- In the Management Console, click Settings -> Destinations -> New Application.
- Select SSH Range.
- In the Name field, enter a meaningful name that identifies the application.
Local Address Range
- Click +Add a Range to add a DNS wildcard or IP range/CIDR.
- Select Enable DNS exclusions to exclude a DNS address from a DNS wildcard. Click here to learn more.
- Click Next.
Note
You can add a DNS wildcard or IP range. The relationship between the wildcards or ranges is an OR relation.
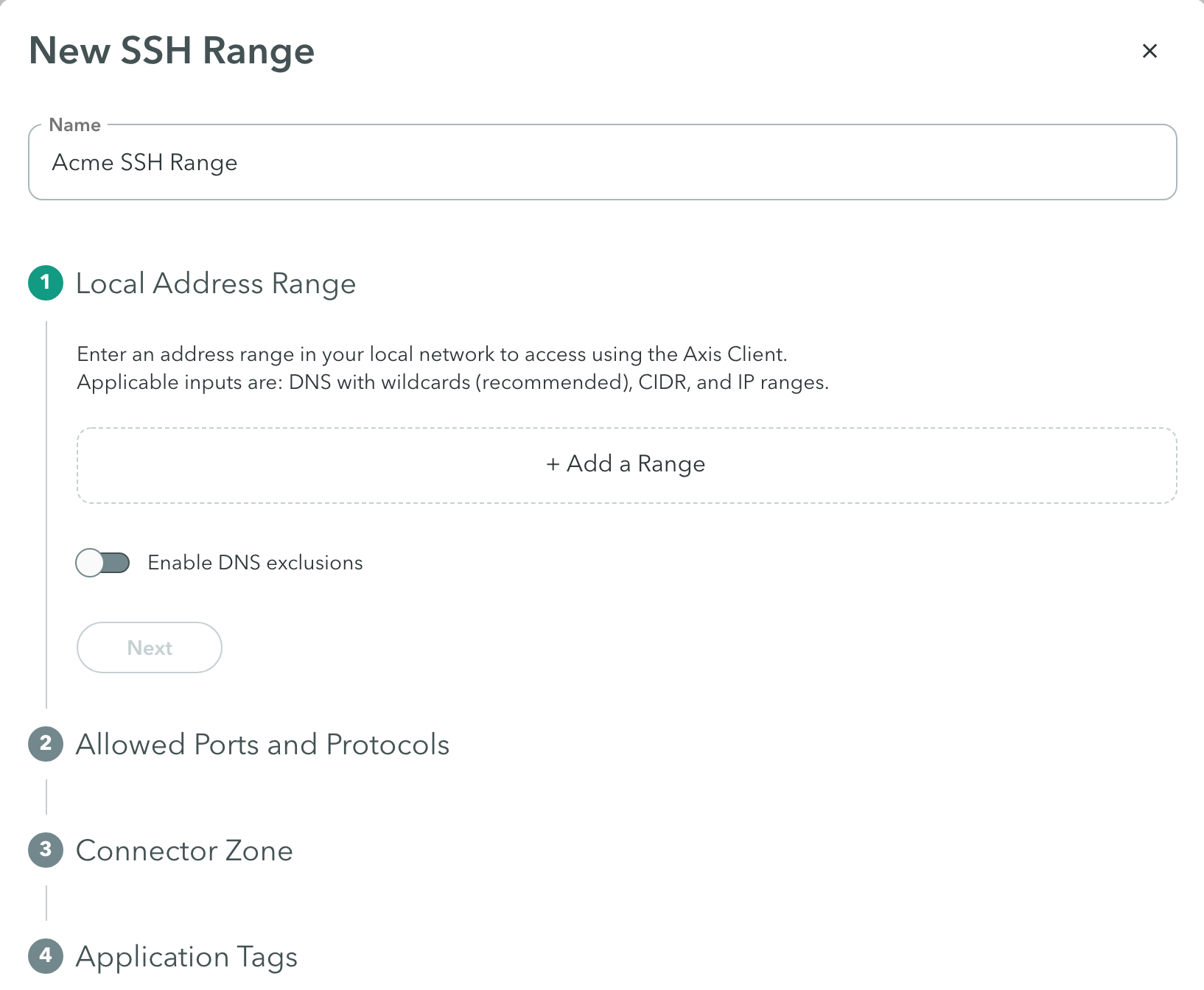
Allowed Ports and Protocols
- Enter port ranges that are relevant for the ranges you entered previously. For SSH servers the standard port is 22.
- For each port range, click the drop-down menu to select the protocol type: UDP, TCP, or both.
- Select the Enable ICMP traffic option to check connectivity on an SSH Range.
- For a list of supported ICMP commands and requirements, click here.
- Click Next
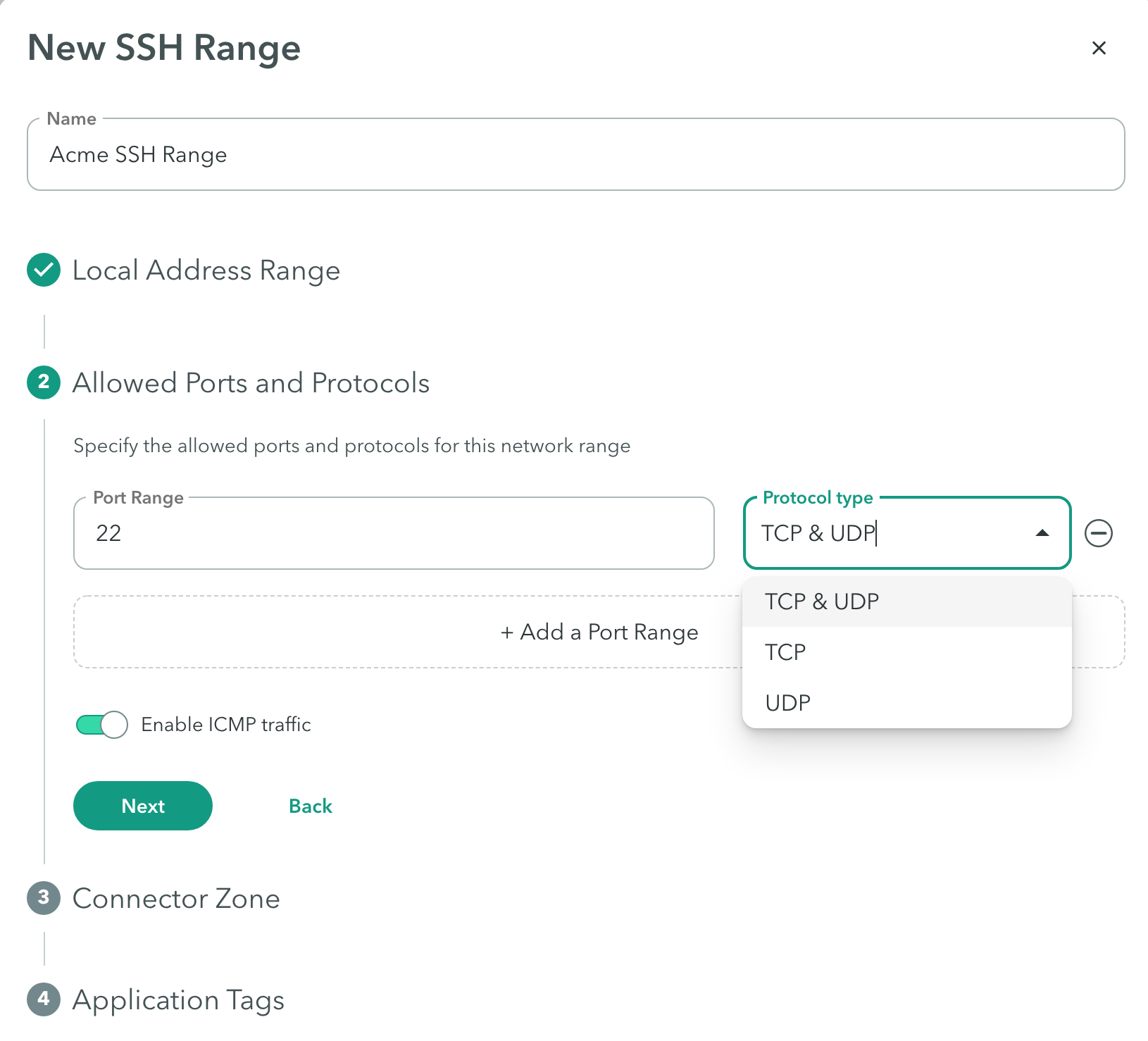
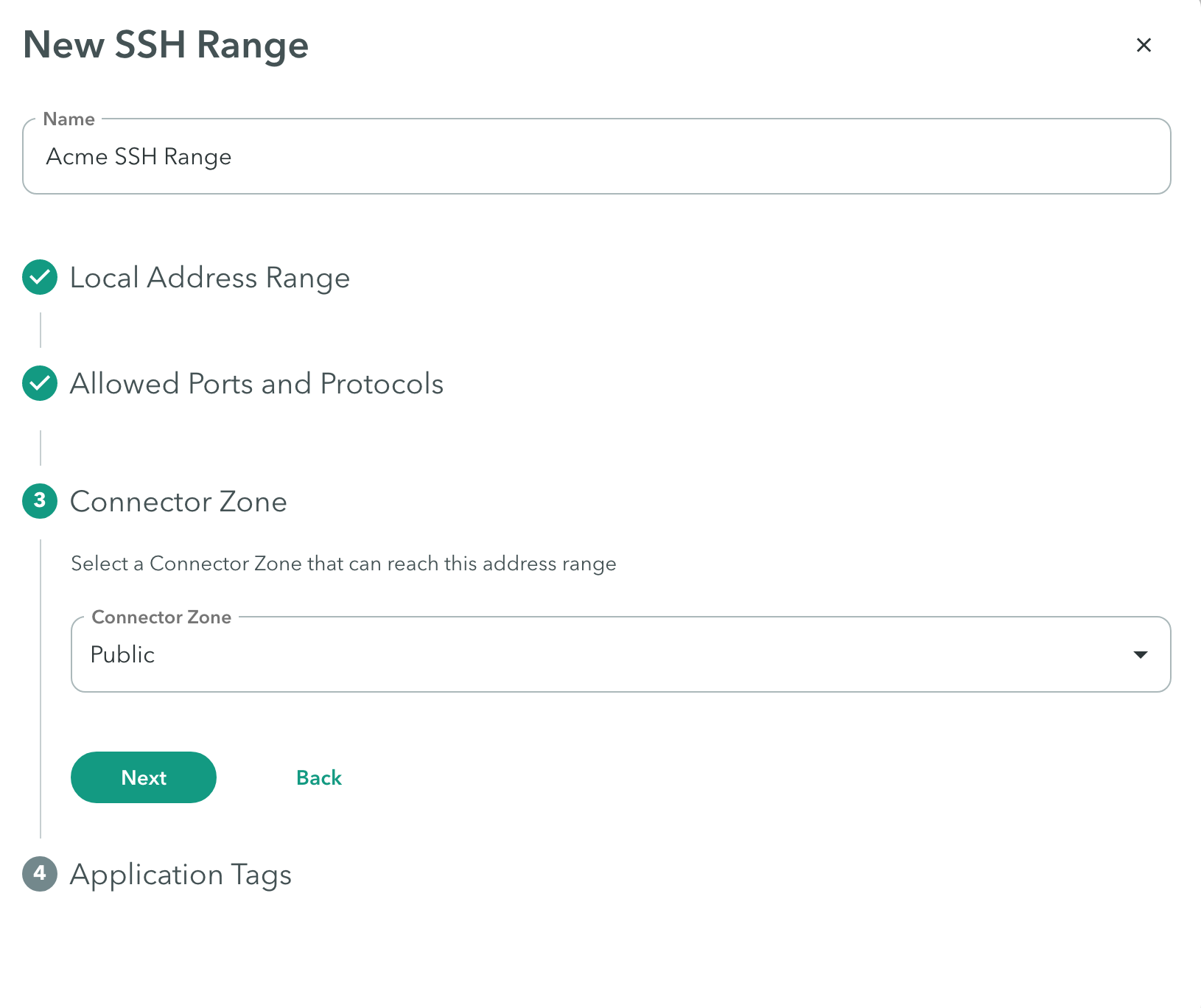
Connector Zone
Configuring a connector zone allows you to connect to a network segment to access applications. Note: When you enable ICMP, use any connector zone, except the Public Connector zone.
To add a connector zone:
- Click the Connector zone drop-down menu to select a Connector Zone that can reach the address range.
- Click Next.
Application Tags (Optional)
Tags help create policy rules fast and efficiently for groups of applications. Click here to learn about creating application tags.
To add application tags:
- Start typing to create new tags, or choose from the Tags drop-down menu.
- Click Submit.
- Click Apply Changes in the top menu bar.
Next steps:
Create a policy to grant access to the application
In general, rules are ordered in importance, with the lowest number (1) having the highest priority. If you have rules that overlap; for example, an SSH Range Application rule and Network Range Application rule, you would place the SSH Range Application rule above the Network Range rule.
For more information about policies, see About Policies and Adding Policy Rules.
Verify that the Atmos Agent is Open and Online
To verify that the Atmos Agent is open and online:
- Use an SSH client such as Terminal or Putty to SSH to the server.
- Use the same username as configured in the User Portal settings as shown in the following example:
SSH user@[server address] - Go to the Insights screen to see that the user has connected to the SSH Range application and which server that the user connected to.
Updated about 2 years ago
