Axis Security ZTNA Solution Versus VPN
Thirty years ago, VPNs emerged to connect a few remote employees to applications located on-premises. Trust was assumed, scalability was not an issue, and the threat landscape was relatively small. Now, the threat landscape has become one of the greatest challenges of our age. While there are still benefits to VPNs, the drive to maintain business resilience, network security, and corporate and customer data integrity are not only critical but essential. Today, VPNs extend network-level privileges to remote users working from home, coffee shops, airports, and other unsecured WiFi locations. Many technologies have been developed in the meantime (NAC, ACLs, VDI, PAM, jump boxes, etc.) to enhance security, but productivity is impacted "because of" management overhead, configuration and deployment complexity, and end-user friendliness that result in productivity losses and a lowered security profile.
For the modern enterprise, Axis Security has introduced a streamlined and frictionless cloud secure remote access solution to connect employees, contractors, and third parties to the specific applications and resources they need to be productive while delivering unmatched security, resilience, and scalability.
This section highlights the differences between Axis Security and traditional VPN solutions. It describes benefits of using Axis Security’s Zero Trust Network Access (ZTNA) to help businesses prosper.
The following illustration shows Axis Security’s key advantages over traditional VPNs.
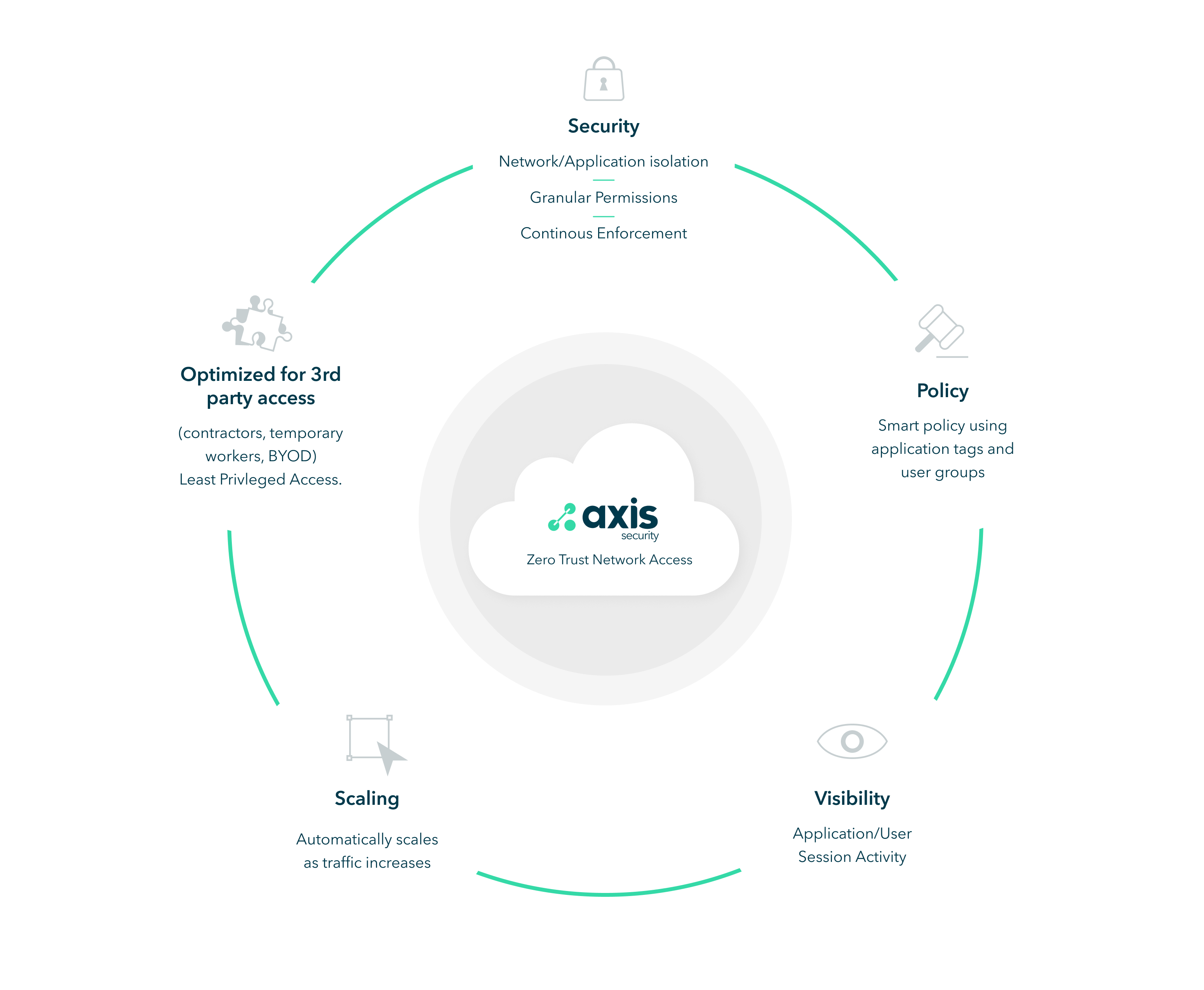
Security
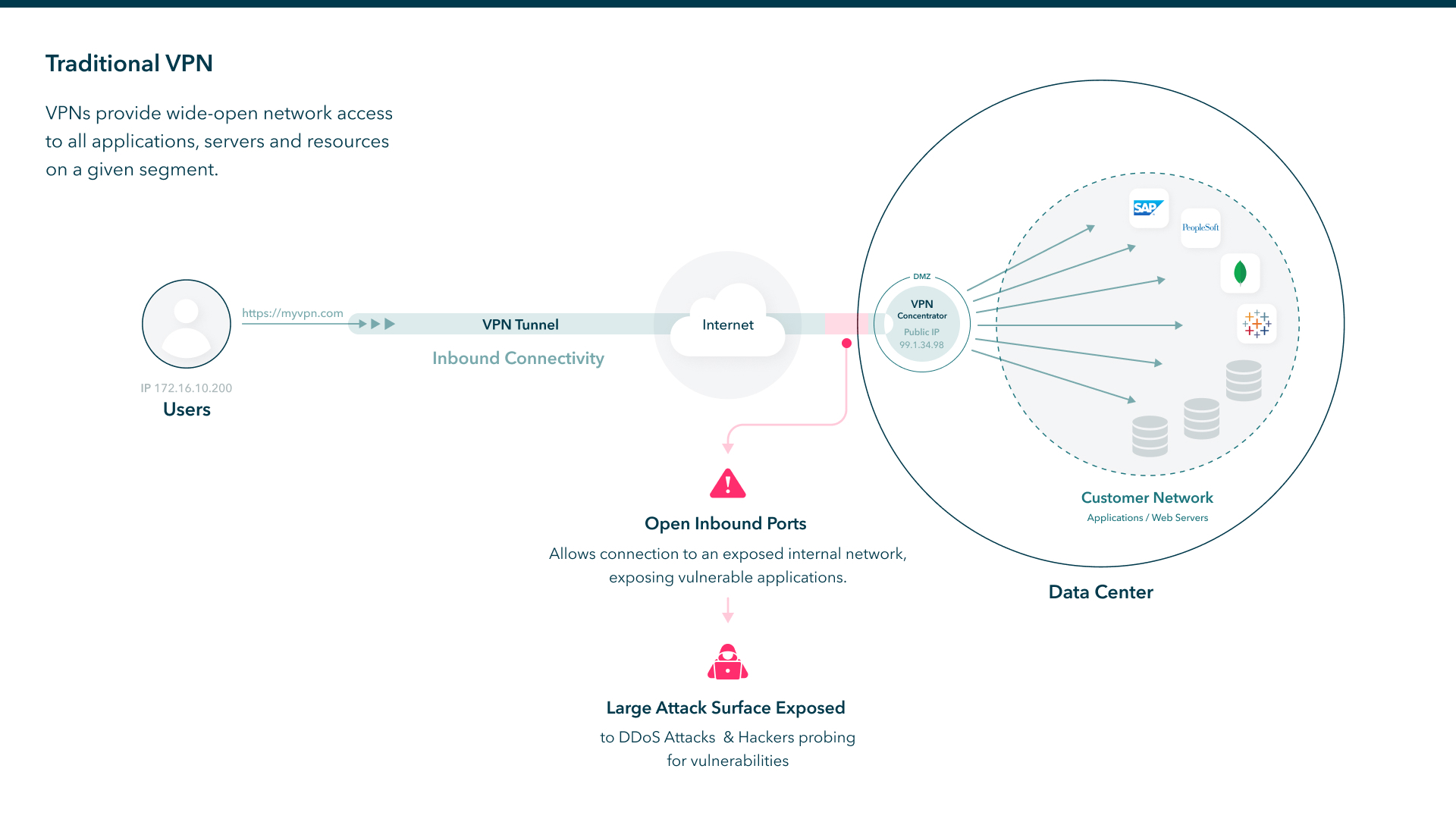
VPNs implicitly allow all traffic to pass. They provide wide-open network access to all applications, servers and resources for a given segment. In contrast, Axis Security uses the Principle of Least Privilege (PoLP) to restrict access to specific applications. It applies granular-access control over user activities at the application level, granting users only the access they need. By limiting access privileges to one or more applications, users can easily be prevented from directly accessing the network. Administrators can retain control of the network and reduce the overall attack surface.
For example, if a user only needs access to a web server, administrators can grant access to this website without access to the network or any other websites that are hosted on this server. If you need access to the network, Axis Security can give you access to specific ranges or domains. This dramatically reduces the attack surface and ensures the right users access the right resources.
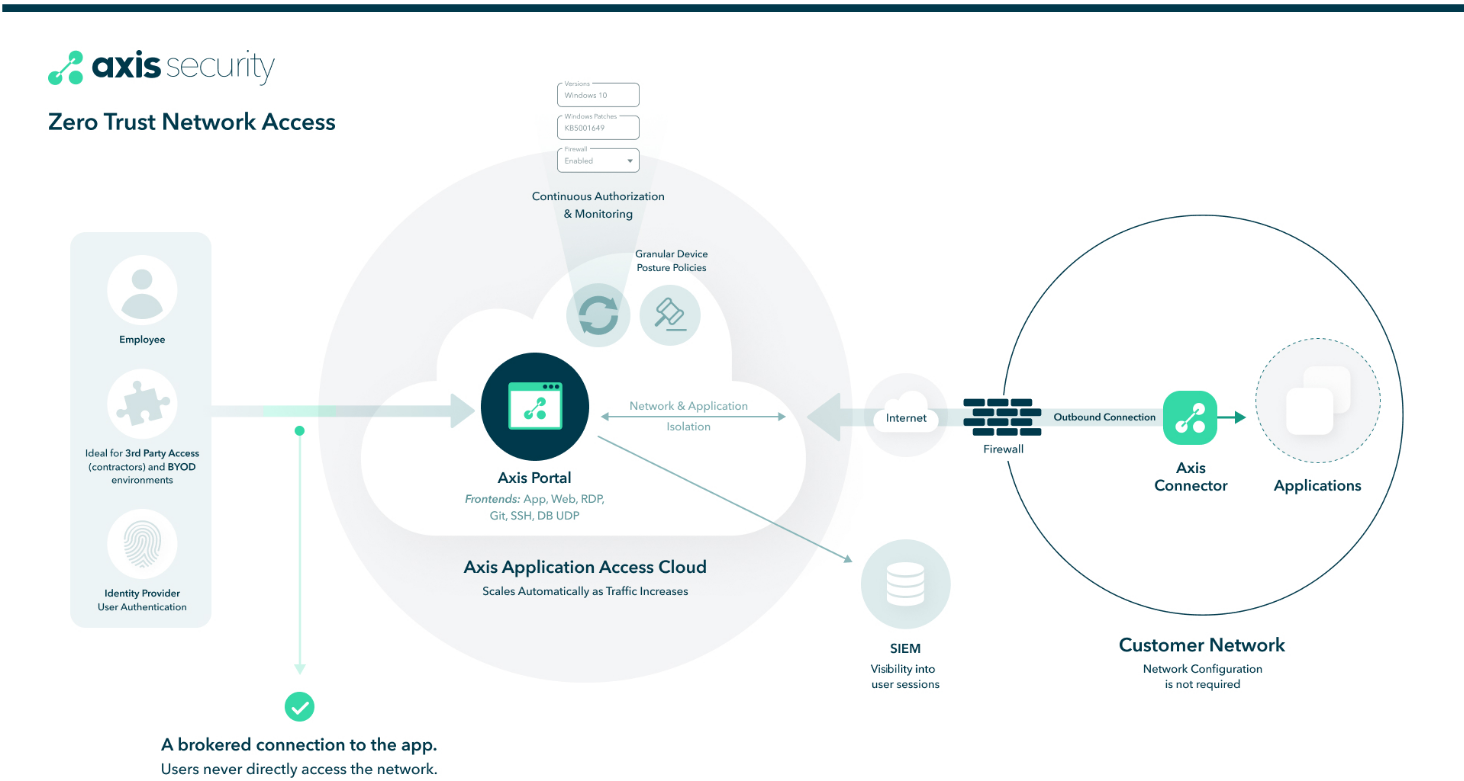
Axis Security isolates the user from the enterprise network entirely by brokering access to applications. It creates an encrypted connection from the user to the Axis Cloud and from the Axis Cloud to the application server. In this way, the user is never directly connected to the network, giving more secure access.
Using a continuous enforcement approach, Axis Security continuously monitors users throughout the session. If a user attempts to access an application during a restricted time or is deleted from your Identity Provider, access is revoked in real-time. These key advantages give you more secure access.
The following diagram illustrates the shortcomings of traditional VPNs.
The following diagram illustrates the key advantages for Axis Security’s ZTNA solution and how Axis Security isolates the user from the enterprise network.
Policy
Axis Security continuously monitors and enforces policies. If a policy parameter changes during a session (for example, a user attempts to access an application from a restricted IP range), the policy is enforced in real-time and the user’s connection is terminated. In contrast, VPNs only apply a policy at the start of the session.
With Axis Security, all access is continuously governed by centrally deployed policies set by the administrator. Administrators can define profiles for the following applications (RDP, SSH, Web App, Git, DB) to simplify creating rules and management. This is useful for provisioning access to specific applications and network segments for specific users or groups. With a large VPN deployment, access is typically controlled by separate VPN concentrators, and as a result, users have to connect to a specific VPN concentrator. In contrast, with Axis Security, users always connect to a global Axis Security’s Application Access Cloud, which brokers traffic seamlessly to applications whatever they are.
With a device posture check, administrators can apply conditions to access applications. Multiple conditions can be applied against a single application. This allows administrators to check the state of all the endpoints that are connecting to the Application Access Cloud (Axis Cloud) for compliance with corporate security policies.
Because the policies are designed with the business-user in mind, they are easy to configure and manage. This reduces administration by simplifying management and offering more granular access control than a traditional VPN, resulting in more secure access.
Visibility
Axis Security logs user actions during each session giving administrators centralized visibility, control, and management into users’ sessions. Administrators can see the applications and URLs accessed, SSH commands issued, files downloaded, and protocols used. With a VPN, administrators only have visibility with the connected IPs; for example, IP address X connected to IP address Y but have no insight into the user's actions (history). Axis Security also gives you the control and flexibility to enable or disable visibility based on your organization's needs.
Scaling
Axis Security scales easier and faster than VPN solutions because it is a cloud-native solution (a SaaS platform). It automatically scales as traffic increases with zero administration, saving time and money. For example, if the number of your users doubles, there are no changes on the Axis Security administration side. VPNs usually require additional VPN concentrators, licenses, patching software updates, network reconfiguration, and in some cases loading additional agents, depending on the solution.
Axis Security can be deployed without installing clients on the endpoints and scales automatically as traffic increases, unlike VPNs. And, it does not require reconfiguring your network, like VPNs do. This solution is ideal for BYOD because they can be easily supported. These key advantages make Axis Security fast to deploy and simple to manage.
Axis Security and VPN Capabilities Comparison
The following table compares Axis Security’s ZTNA Solution with a Traditional VPN.
| Capabilities | Axis | VPN |
|---|---|---|
| Policy: Granular Access The platform provides granular policy access to specific applications, including: Device Posture Checks, such as personal firewall and disk encryption check Conditions, such as destinations, time of day, location, and IP address range. | Yes | No |
| Continuous Enforcement The platform ensures continuous authentication throughout the session and not only at initial login. | Yes | No |
| 3rd party Limited Access The platform allows administrators to restrict access for contractors, temporary employees, BYOD devices. Axis Security can grant different access to different users and groups using device posture and conditions | Yes | No |
| Network Isolation The platform restricts access to individual applications rather than whole networks | Yes | No |
| Application Isolation Applications are published through the platform and are not exposed directly to the internet. See Architecture Architecture]. VPN exposes your access point via public IP that can be easily scanned to determine your finger print of your access point and makes you vulnerable to DDoS attacks. | Yes | No |
| Visibility: Insights into User Activity The platform tracks all user activity to provide detailed views of network and application behavior, including URL history, SSH commands and file downloads. | Yes | No |
| Auto scaling The platform scales automatically as traffic increases without network reconfiguration. | Yes | No |
Updated 10 months ago
