Adding Trusted Sources
Use the Trusted Sources option for API-based, HTTP and HTTPS traffic server-to-server communication from a trusted resource without going through IdP authentication.
Note
This is a limited release feature.
Important
This option restricts access to specific IPs (without authentication or policy checking). Other sources will not be allowed to access the application.
This section has the following topics:
- Configuring a Trusted Sources Authentication Exemption
- Viewing Trusted Sources Activity
Configuring a Trusted Sources Authentication Exemption
To configure a Trusted Sources Authentication Exemption:
- In the Management Console, navigate to the Settings > Destinations > New Application > Web Applications > Self-Hosted Web Application.
- In the bottom right of the New Hosted Web Application screen, click Advanced Settings.
The Advanced Settings screen is displayed.
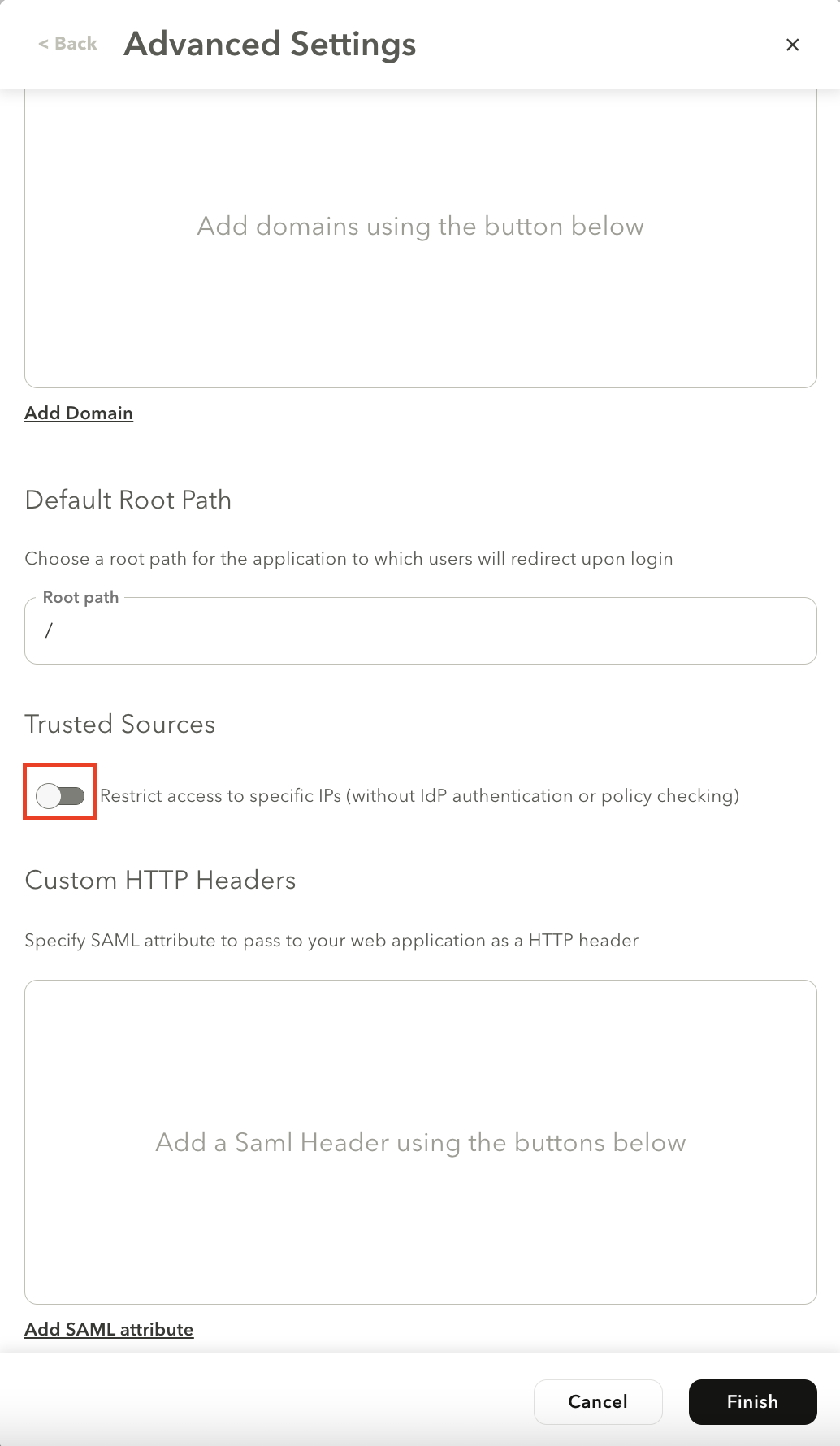
- In the Trust Sources section, select the Restrict access to specific IPs (without IdP authentication or policy checking) toggle to enable the feature.
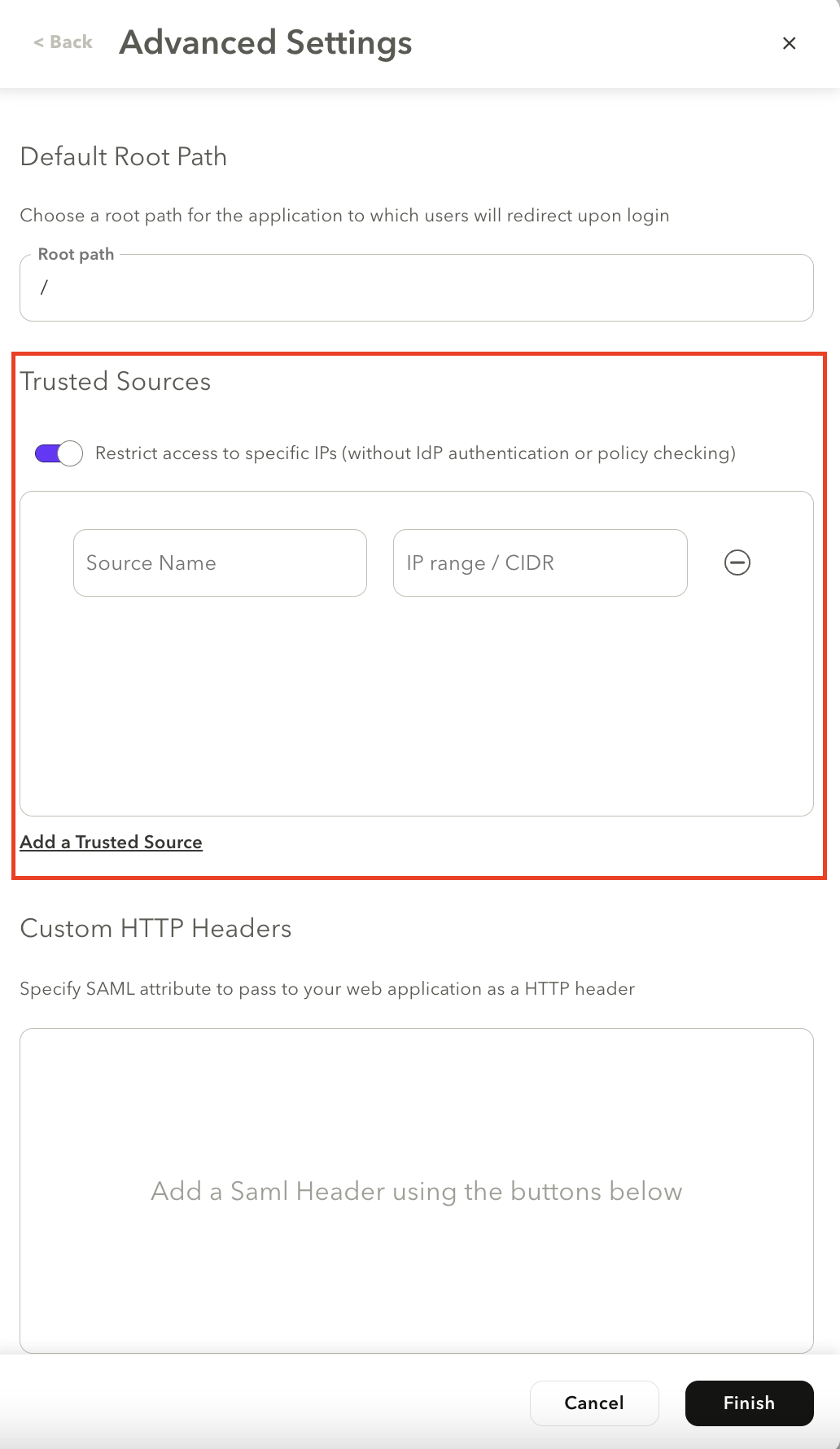
- Click Add a Trusted Source.
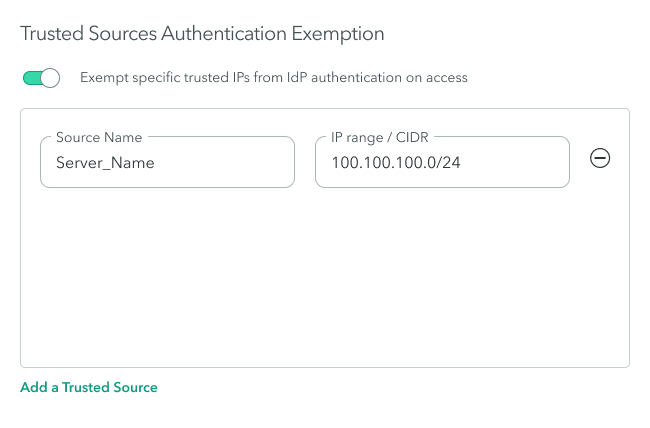
- In the Source Name, enter the source name.
- In the IP range/CIDR, enter the IP range or CIDR.
Important
When specifying the source IP Range/CIDR, make sure that it is a trusted source that you want to exempt from IdP authentication.
- Save your changes.
- In the top right of the screen, select Apply Changes > Commit Changes.
- Next Steps: Viewing Trusted Sources Activity
Viewing Trusted Sources Activity
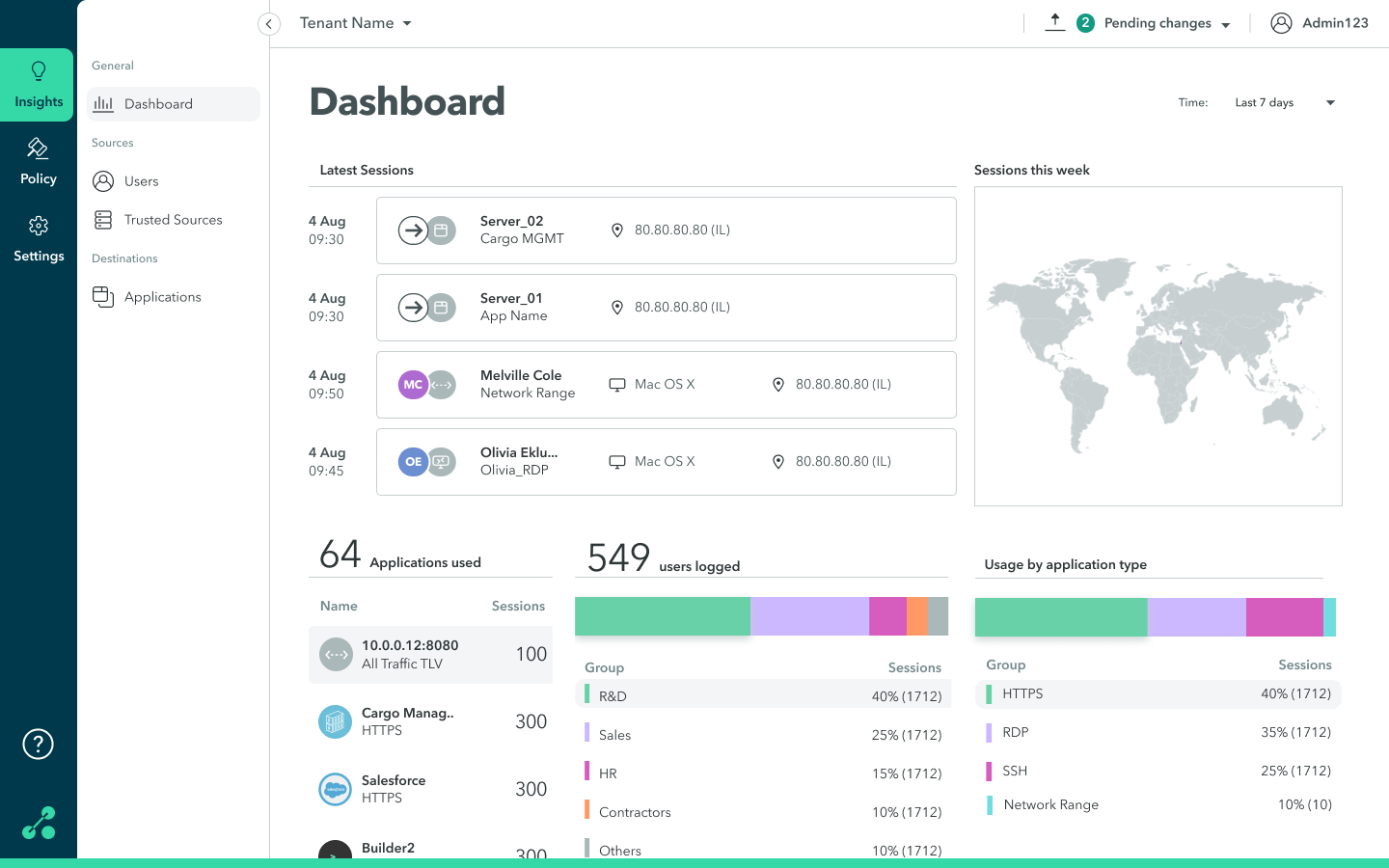
You can view trusted source sessions, including the IP address, location, and duration of the session. You can view trusted source sessions in the Dashboard and activity in the Trusted Sources screen.
To view trusted sources sessions in the Dashboard, navigate to the Insights > Dashboard screen.
To view trust source activity:
- Navigate to the Insights > Trusted Sources screen.
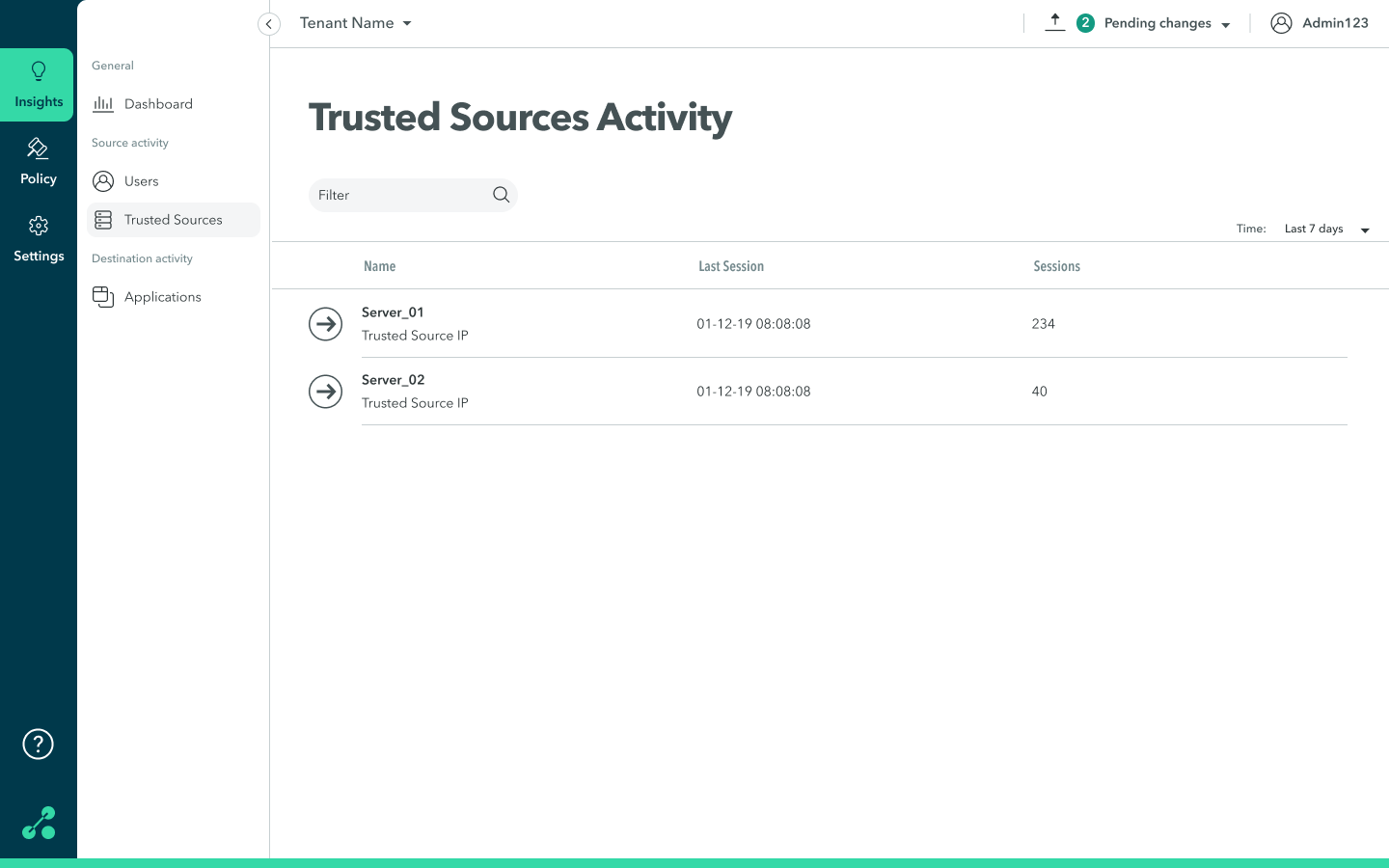
-
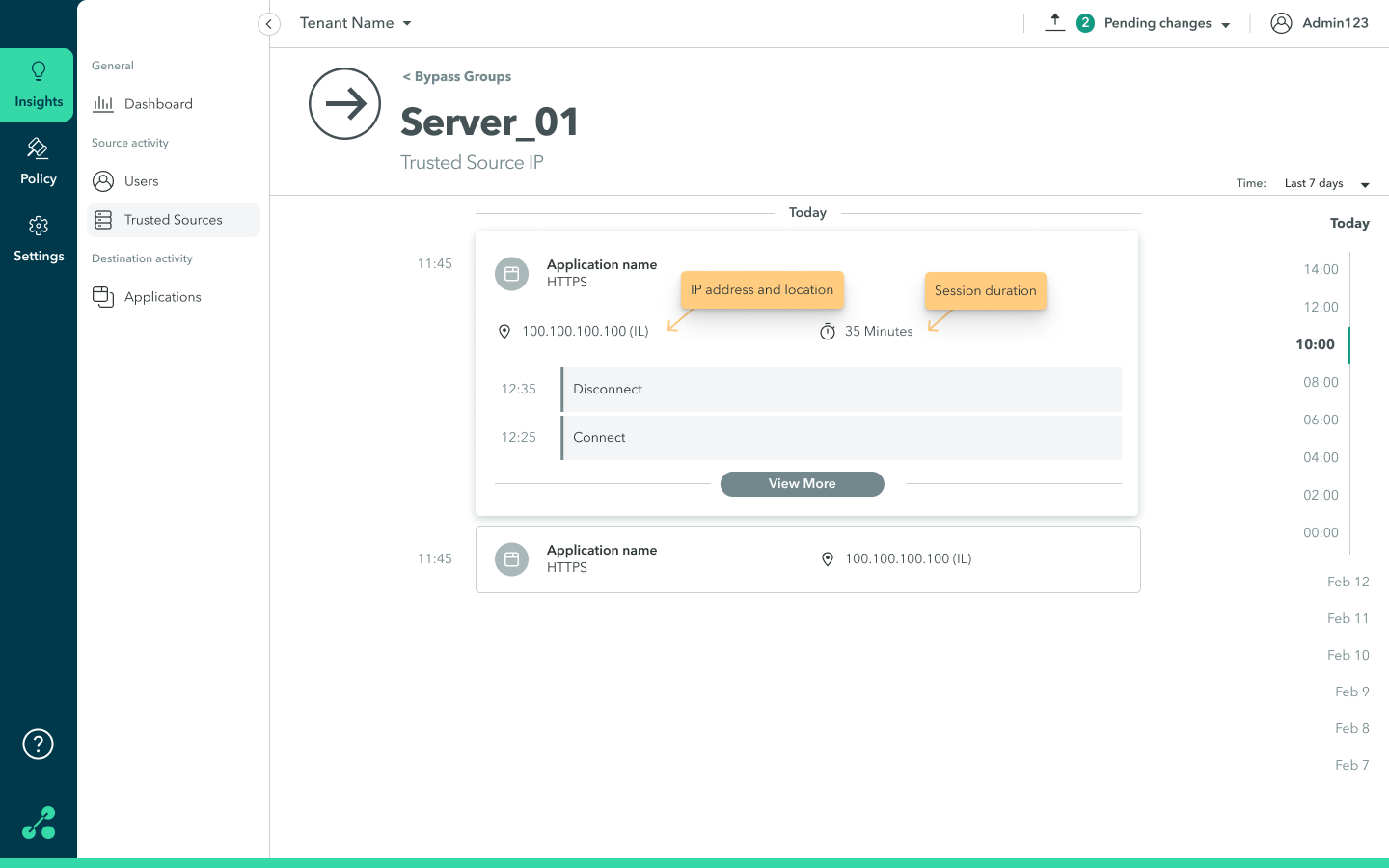
On the trusted resource, click anywhere in the row to view detailed information about the trusted resource (IP address, location, and duration of session).
The following screen is displayed.
Updated almost 2 years ago
