About Axis
Axis Atmos Cloud securely connects any user to any business application or resource, wherever they are in minutes through a single, centrally managed service. Axis provides continuous, application-centric visibility and Zero Trust controls to enable and secure organizations in today’s age of digital transformation, work-from-anywhere, and integrated employee/contractor/third-party business models. See also Feature Comparison: Atmos Agent Versus Atmos Air.
What is Atmos Cloud?
Atmos Cloud is a zero-trust agent-less access broker for employees, partners and other stakeholders that allows access to corporate resources from any device, anywhere. It provides granular visibility, continuous authorization and analytics over data and applications used throughout each session.
Unlike legacy solutions such as VPNs that overshare access and create excess risk to users, networks and data, Axis’ unique Application Isolation Technology ensures users only gain access to what’s allowed. It vigilantly monitors every application communication for risk. The result is friction-less user access and total security control for enterprise IT.
The following illustration shows Atmos Cloud as a Security Service Edge (SSE), which provides a single unified platform for all application access while decoupling application access from the corporate network.
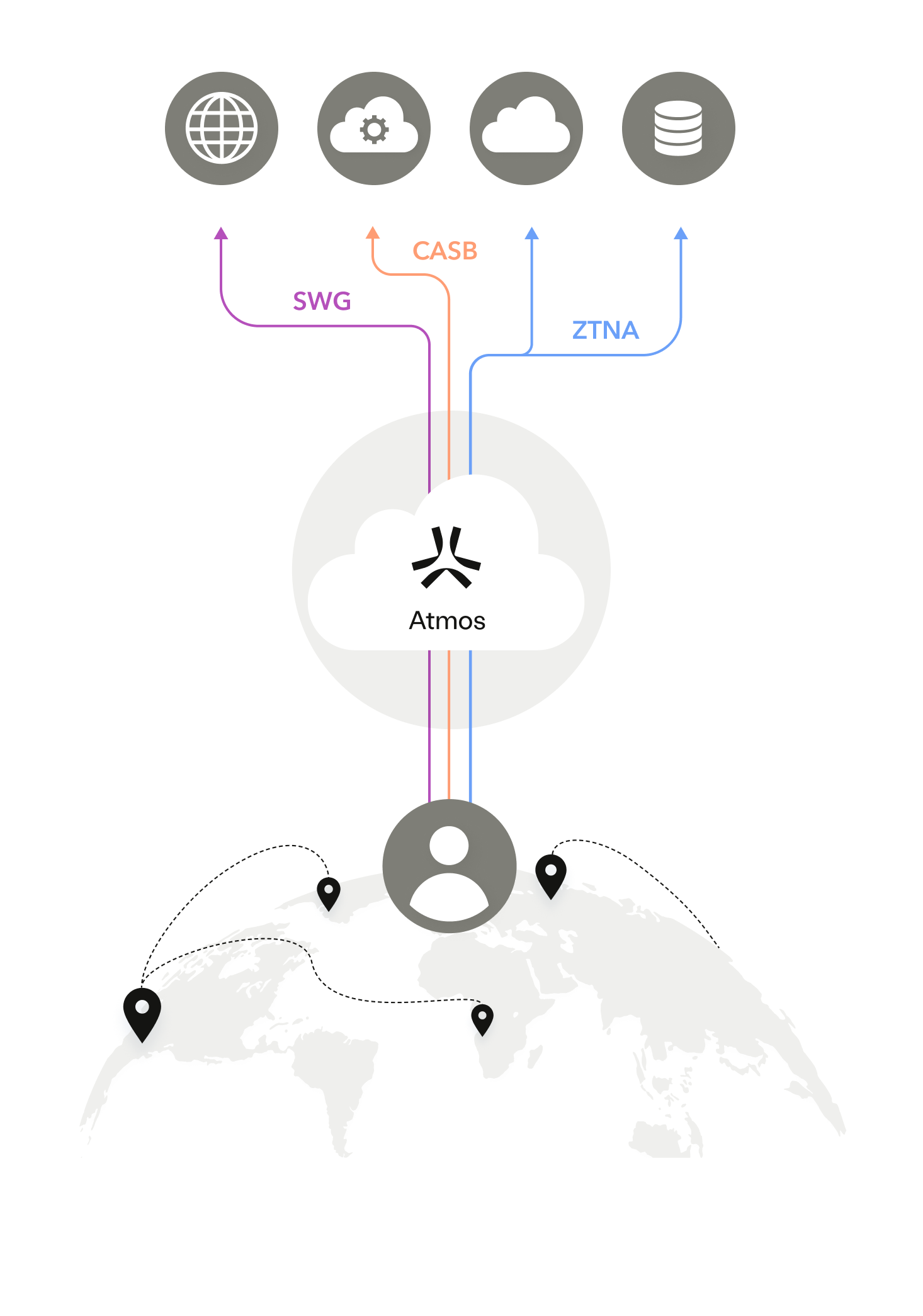
The Atmos Cloud Value
Atmos Cloud value provides the following unique benefits:
- Reduces the attack surface and bad actor lateral movement across a network
- Eliminates network scans and attacks on infrastructure
- Minimizes the potential for credential-based compromise (often harder to detect)
- Enables painless, secure and as needed access to apps and data from any device, improving remote work productivity and user experience overall
- Provides true user session visibility, enabling greater access and user behavior control, business-ready analytics, and complete session recording
- Provides a flexible approach to rapidly detect and respond to malicious events
- Uses an agent-less approach that streamlines implementation and maintenance efforts, allowing for quick value realization
The following illustration shows that users who work in the office, or work in a hybrid context receive the same zero trust standard and consistent access experience.
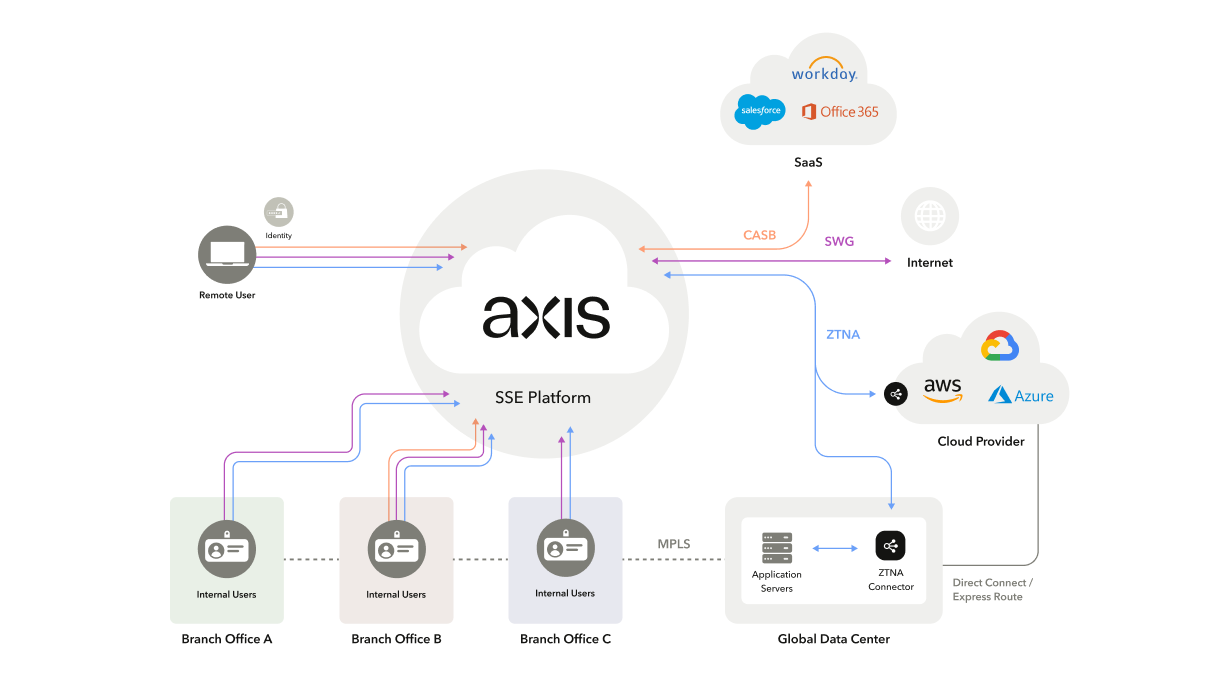
For more information, see The Architect’s Guide to Adopting Security Service Edge (SSE) Adopting Security Service Edge (SSE).
Updated 9 months ago
